The InCommon Certificate Service FAQ This document subject to change as elements of the program are refined.
|
|
|
- Adam Webb
- 8 years ago
- Views:
Transcription
1 The InCommon Certificate Service FAQ InCommon is an LLC of Internet2 October 13, 2010 This document subject to change as elements of the program are refined. 1. What is the InCommon Certificate Program? 2. Who can subscribe to the InCommon Cert Service? 3. When will this program be available? 4. Why is this program attractive to my institution? 5. What is Comodo s role in this service? 6. Are there any types of certificates excluded from this program? 7. How will institutions sign up for this program? 8. What if my campus operates domains other than their primary institutional.edu domain? 9. What is the required term of participation? 10. Why are Internet2 members being given a 25 percent discount for participation? 11. Why is InCommon membership required for participation? 12. How will institutions actually acquire certificates? 13. What types of interfaces will an institution have to Comodo for certificate issuance and general program administration? 14. How many certificate profiles will be supported and what do they cover? 15. Can I have my own Campus Root issued under the InCommon hierarchy? 16. Will the certificates issued via this program be recognized in other federations? 17. What are the supported browsers, devices and application suites? 18. Are non-profit regional research and education networks and other organizations within the.edu domain eligible?
2 The InCommon Certificate Service FAQ InCommon is an LLC of Internet2 Revision 3.1 October 13, 2010 This document subject to change as elements of the program are refined. 1. What is the InCommon Certificate Program? The InCommon Cert Service, created by and for the higher education community, provides unlmited server and personal certificates at one low fee. This includes unlimited SSL, personal signing, EV, encryption and code signing PKI certificates. Internet2 members receive a 25 percent discount. 2. Who can subscribe to the InCommon Cert Service? Any higher education institution with its primary location in the United States, and that qualifies for a primary domain name in.edu, may subscribe, as well as not-for-profit regional research and education networking organizations in the United States. Subscribers must be InCommon participants or must join InCommon. 3. When will this program be available? The SSL (or server cert) portion of the program is available now. Unlimited person certs will be available in late fall Why is this program attractive to my institution? The higher education community developed this service to reduce the cost of certificates. Because InCommon is a non-profit, community-driven organization, the primary drivers are to provide value an benefits to the subscribers (rather than providing profit for the certificate provider). The program offers unlimited certs at one annual fee, which is expected to reduce the cost of certificates for many institutions. 5. What is Comodo s role in this service? Comodo is the certificate authority and InCommon has contracted with Comodo for the deep discounts available to colleges and universities. As a commercial CA, Comodo has extensive knowledge of the marketplace and attractive features. Comodo has been operating a similar service with TERENA, the Trans-European Research and Education Networking Association. TERENA s positive association with Comodo, and its significant software development for the Comodo APIs, made this partnership attractive to InCommon and Internet2. 6. Are there any types of certificates excluded from this program? This program includes all certificates listed in #1 above. The program allows institutions to issue so-called wild-card certificates. A primary attraction of wild-carts certs has been to allow a reduction of the number of certs purchased. Given that in this program there is no longer a price penalty for issuance of additional SSL certs, institutions may want to reconsider the use of wild-card certs, as some security experts believe that such certs reduce security due to the extra burden of managing private keys in multiple locations. 7. How will institutions sign up for this program? There is a Certificate Service Subscriber Agreement that is an addendum to the InCommon Federation participation agreement. The subscriber agreement, including the associated terms and conditions, is available at InCommon participation is required to take advantage of the certificate service. 8. What if my campus operates domains other than their primary institutional.edu domain?
3 Any domains administered by the institution (e.g., a professional society with a.org domain or even a.com domain) can qualify, as long as the institution can prove that it is the administrative manager for that organization. The key requirement is that the institution be the administrator of record for these domains and organizations. 9. What is the required term of participation? Initially, institutions are required to commit to participation for an initial term of three (3) years, with the cert service fee billed annually. 10. Why are Internet2 members being given a 25 percent discount for participation? InCommon is wholly owned by Internet2 and Internet2 is providing the initial capital required to launch the program. 11. Why is InCommon membership required for participation? This program is an extension of the trust services already being provided and managed by InCommon, and will require InCommon resources, including staff time and effort. In particular, implementation of this program will take advantage of the Registration Authority (RA) already managed by InCommon in establishing the trust services structure with participants. 12. How will institutions actually acquire certificates? InCommon will undertake the Registration Authority responsibilities of the program, leveraging its current processes for verifying organizations and identity proofing officials authorized to act on behalf of an institution for certificate issuance. These individuals may be the same or different than the current InCommon administrators. It is expected that at each institution a small number of people (typically two or three) will be authorized to manage the overall institutional certificate program. Once an institution authorizes individuals, they will deal directly with the Comodo CA (via either a GUI or API) for requesting individual certificates. InCommon is, by design, not in the path of certificate issuance or revocation (or even in the path of authorizing second-level personnel), only the vetting of the top-level certificate program administrators and the domains they are authorized to administer. 13. What types of interfaces will an institution have to Comodo for certificate issuance and general program administration? Comodo offers both a GUI (called the Comodo Certificate Services Manager, CSM) and an API to their service for certificate issuance, management of second-level personnel and institutional policies for certificate structure, as well as support in matters such as certificate revocation. 14. How many certificate profiles are supported and what do they cover? There are seven (7) profiles available to participants: 1. SSL Server certificate (standard TLS cert includes certs with SANs) 2. SSL Wildcard certificate (TLS cert with a wildcard CN) 3. EV Server Certificate issued directly by Comodo and subject to Comodo s domain vetting processes, terms and conditions and CPS, but at no extra charge beyond the base InCommon cert service fee. 4. Code Signing certificate (for signing software that can be trusted when distributed with, e.g., jar files, etc.) 5. User certificate (Digital Signature) (for signing , documents, or authenticating to PKI based services) 6. User certificate (Encryption) (for encrypting , documents, or symmetric keys used to secure data see escrow information above) 7. User certificate (Dual Use) (a combination of the above two see escrow information above; escrow of dual use certificates is potentially problematic however because it does eliminate the non-repudiation characteristic of signing certificates)
4 15. Can I have my own Campus Root issued under the InCommon hierarchy? The initial release of this program does not provide this functionality, but this option is available under the agreement with Comodo. When the GUI for certificate life cycle management has the capability of supporting this option, it is anticipated that institution-based subordinate CAs (and campus-specific profiles and practice statements) will be made available to members who desire this functionality for an additional cost. 16. Will the certificates issued via this program be recognized in other federations? This functionality is anticipated for a later release of the program based on the demand from the InCommon community. The agreement with Comodo allows for cross-signing of other CAs at an additional cost. 17. Comodo Supported Browsers, Devices and Application Suites: Extended Validation Browsers: Microsoft Internet Explorer 7 + Opera 9.5+ Firefox 3+ Apple Safari 3.2+ Google Chrome 1+ Web Browsers: Microsoft Internet Explorer Mozilla Firefox 1.0+ Opera 8.0+ Apple Safari Google Chrome AOL 5 + Netscape Communicator Camino 1.0+ Konqueror (KDE) Mozilla Clients (S/MIME): Microsoft Outlook 99+ Microsoft Entourage (OS/X) Mozilla Thunderbird 1.0+ Microsoft Outlook Express 5+ Qualcomm Eudora 6.2+ Lotus Notes (6+) Mail.app (Mac OS X) Microsoft / Windows Mail 1.0+ (Vista) The Bat 1+ Micro Browsers /PDAs Apple iphone ipod Safari 1.0+ Microsoft Windows Mobile 5* / 6 + ACCESS NetFront Browser v3.4 + RIM Blackberry v KDDI Openwave v Opera Mini v3+ Opera Mobile 6+ Sony Playstation Portable Sony Playstation 3 Netscape Communicator Nintendo Wii NTT / DoCoMo Application Suites:
5 Microsoft Authenticode Visual Basic for Applications (VBA) Adobe AIR Sun Java SE Mozilla Suite 1.0+ Sea Monkey Document Security Platforms: Microsoft Office (Word, Excel,Powerpoint, Access, InfoPath) Server Platforms All SSL-Capable Server Platforms * Windows Mobile 5 certificates will be issued from a Non InCommon / Internet 2 branded subordinate Root. 18. Are non-profit regional research and education networks and other organizations within the.edu domain eligible? Not for profit regional research and education networking organizations with primary offices in the United States that are not housed within an otherwise eligible educational institution may join this program by paying an annual fee of $2,000. No further discounts are applicable to this fee. In all cases, participation in this program is solely to allow the organization to acquire certificates for staff within that organization and for servers and services operated directly by the organization. Participation explicitly excludes the ability for the organization to issue certificates to members of the organization or to resell the service to members of the organization. This fee also applies to any non-carnegie classified organizations who qualify for participation (i.e., organizations in the United States who currently have a.edu domain). All participating organizations must still join InCommon as is required for all participants in this program.
The InCommon Certificate Service
 The InCommon Certificate Service January 2011 Joint Techs Randall Frank Internet2 The Basic Program Internet2 through its InCommon Trust Services division now offer unlimited SSL certs (including EVcerts,
The InCommon Certificate Service January 2011 Joint Techs Randall Frank Internet2 The Basic Program Internet2 through its InCommon Trust Services division now offer unlimited SSL certs (including EVcerts,
Comodo 2048 bit SSL Certificates. Security for your online business now and long into the future
 Security for your online business now and long into the future Today, online commerce is worth over US $1 trillion and continues to grow at a substantial rate. SSL Certificates are a cornerstone of this
Security for your online business now and long into the future Today, online commerce is worth over US $1 trillion and continues to grow at a substantial rate. SSL Certificates are a cornerstone of this
Realize Greater Profits As An Authorized Reseller Of Network Solutions nsprotect Secure SSL Certificates
 Network Solutions Secure Services Realize Greater Profits As An Authorized Reseller Of Network Solutions nsprotect Secure s The Federal Trade Commission (FTC) estimates that 3.2 million US citizens every
Network Solutions Secure Services Realize Greater Profits As An Authorized Reseller Of Network Solutions nsprotect Secure s The Federal Trade Commission (FTC) estimates that 3.2 million US citizens every
Tidspunkt 18-08-2015 11:58 01-07-2015 00:00-18-08-2015 23:59 (49 dag(e)) Operativsystem (OS) fordelt på browsere Total: 267852. Safari9 ios 7921 100%
 Indstillinger Tidspunkt 18-08-2015 11:58 Periode 01-07-2015 00:00-18-08-2015 23:59 (49 dag(e)) Operativsystem (OS) fordelt på browsere Total: 267852 Safari9 ios 7921 100% MAC OS X 1 0% Safari8 ios 572
Indstillinger Tidspunkt 18-08-2015 11:58 Periode 01-07-2015 00:00-18-08-2015 23:59 (49 dag(e)) Operativsystem (OS) fordelt på browsere Total: 267852 Safari9 ios 7921 100% MAC OS X 1 0% Safari8 ios 572
SSL Certificates Enrollment, Collection, Installation and Renewal Release Date: May, 2015
 Version 5.4 SSL Certificates Enrollment, Collection, Installation and Renewal Release Date: May, 2015 InCommon c/o Internet2 1000 Oakbrook Drive, Suite 300 Ann Arbor MI, 48104 Enrolling For Your Certificate
Version 5.4 SSL Certificates Enrollment, Collection, Installation and Renewal Release Date: May, 2015 InCommon c/o Internet2 1000 Oakbrook Drive, Suite 300 Ann Arbor MI, 48104 Enrolling For Your Certificate
Overview of DFN`s Certificate Services - Regular, Grid and short-lived -
 Overview of DFN`s Certificate Services - Regular, Grid and short-lived - Marcus Pattloch (DFN-Verein) DESY Computing Seminar 13. July 2009, Hamburg Overview Certificates what are they good for (and what
Overview of DFN`s Certificate Services - Regular, Grid and short-lived - Marcus Pattloch (DFN-Verein) DESY Computing Seminar 13. July 2009, Hamburg Overview Certificates what are they good for (and what
BHARAT HEAVY ELECTRICALS LIMITED
 BHARAT HEAVY ELECTRICALS LIMITED SCOPE &TECHNICAL SPECIFICATIONS FOR SECURITY CERTIFICATE SPECIFICATION NUMBER: PE888S-1202 REV.01 PROJECT ENGINEERING MANAGEMENT DIVISION PPEI BUILDING, HRDI & ESI COMPLEX
BHARAT HEAVY ELECTRICALS LIMITED SCOPE &TECHNICAL SPECIFICATIONS FOR SECURITY CERTIFICATE SPECIFICATION NUMBER: PE888S-1202 REV.01 PROJECT ENGINEERING MANAGEMENT DIVISION PPEI BUILDING, HRDI & ESI COMPLEX
Q. I use a MAC How do I change my password so I can send and receive my email?
 Password Change FAQ Q. I use a MAC How do I change my password so I can send and receive my email? A. First point a browser to http://www.redlands.edu/passwordmanager and change your password. Afterward,
Password Change FAQ Q. I use a MAC How do I change my password so I can send and receive my email? A. First point a browser to http://www.redlands.edu/passwordmanager and change your password. Afterward,
Comodo Certification Practice Statement
 Comodo Certification Practice Statement Comodo CA, Ltd. Version 3.0 22 September 2006 3rd Floor, Office Village, Exchange Quay, Trafford Road, Salford, Manchester, M5 3EQ, United Kingdom Tel: +44 (0) 161
Comodo Certification Practice Statement Comodo CA, Ltd. Version 3.0 22 September 2006 3rd Floor, Office Village, Exchange Quay, Trafford Road, Salford, Manchester, M5 3EQ, United Kingdom Tel: +44 (0) 161
Overview of Extended Validation (EV) SSL
 Extended Validation SSL Order Guide 1 Ordering Guide for Extended Validation SSL 1. Vetting Preparation 2. CSR Generation 3. Online Ordering Process 4. Vetting Process 5. Receiving & Installing your Certificate
Extended Validation SSL Order Guide 1 Ordering Guide for Extended Validation SSL 1. Vetting Preparation 2. CSR Generation 3. Online Ordering Process 4. Vetting Process 5. Receiving & Installing your Certificate
BEGINNERS GUIDE TO SSL CERTIFICATES: Making the BEST choice when considering your online security options
 BEGINNERS GUIDE TO SSL CERTIFICATES: Making the BEST choice when considering your online security options BEGINNERS GUIDE TO SSL CERTIFICATES Introduction Whether you are an individual or a company, you
BEGINNERS GUIDE TO SSL CERTIFICATES: Making the BEST choice when considering your online security options BEGINNERS GUIDE TO SSL CERTIFICATES Introduction Whether you are an individual or a company, you
Apple Inc. Certification Authority Certification Practice Statement Worldwide Developer Relations Version 1.14 Effective Date: September 9, 2015
 Apple Inc. Certification Authority Certification Practice Statement Worldwide Developer Relations Version 1.14 Effective Date: September 9, 2015 Table of Contents 1. Introduction... 5 1.1. Trademarks...
Apple Inc. Certification Authority Certification Practice Statement Worldwide Developer Relations Version 1.14 Effective Date: September 9, 2015 Table of Contents 1. Introduction... 5 1.1. Trademarks...
Secure Outgoing Mail (SMTP) Setup Guide
 Secure Outgoing Mail (SMTP) Setup Guide Mozilla Thunderbird Windows* 1. Load Mozilla Thunderbird. 2. In the Tools pull-down menu select Account Settings 3. In the left hand panel select Outgoing Server
Secure Outgoing Mail (SMTP) Setup Guide Mozilla Thunderbird Windows* 1. Load Mozilla Thunderbird. 2. In the Tools pull-down menu select Account Settings 3. In the left hand panel select Outgoing Server
COMODO CERTIFICATE MANAGER. Simplify SSL Certificate Management Across the Enterprise
 COMODO CERTIFICATE MANAGER Simplify SSL Certificate Management Across the Enterprise Comodo Certificate Manager CCM Enables nominated administrators the ability to manage the lifespan, issuance, deployment,
COMODO CERTIFICATE MANAGER Simplify SSL Certificate Management Across the Enterprise Comodo Certificate Manager CCM Enables nominated administrators the ability to manage the lifespan, issuance, deployment,
Email Client Configuration Secure Socket Layer. Information Technology Services 2010
 Email Client Configuration Secure Socket Layer Information Technology Services 2010 Table of Contents A. Apple Mail [Mac OSX Leopard]... 1 1. POP SSL Secure Settings... 1 2. IMAP SSL Secure Settings...
Email Client Configuration Secure Socket Layer Information Technology Services 2010 Table of Contents A. Apple Mail [Mac OSX Leopard]... 1 1. POP SSL Secure Settings... 1 2. IMAP SSL Secure Settings...
Bugzilla ID: Bugzilla Summary:
 Bugzilla ID: Bugzilla Summary: CAs wishing to have their certificates included in Mozilla products must 1) Comply with the requirements of the Mozilla CA certificate policy (http://www.mozilla.org/projects/security/certs/policy/)
Bugzilla ID: Bugzilla Summary: CAs wishing to have their certificates included in Mozilla products must 1) Comply with the requirements of the Mozilla CA certificate policy (http://www.mozilla.org/projects/security/certs/policy/)
Comodo 2048 bit SSL Certificates. Security for your online business now and long into the future
 Security for your online business now and long into the future Today, online commerce is worth over US $1 trillion and continues to grow at a substantial rate. are an indispensable cornerstone of this
Security for your online business now and long into the future Today, online commerce is worth over US $1 trillion and continues to grow at a substantial rate. are an indispensable cornerstone of this
Test Plan for Department of Defense (DoD) Public Key Infrastructure (PKI) Interagency/Partner Interoperability. Version 1.0.3
 Test Plan for Department of Defense (DoD) Public Key Infrastructure (PKI) Interagency/Partner Interoperability Version 1.0.3 Prepared for: Department of Defense (DoD) PKI August 27, 2008 Page 1 Table of
Test Plan for Department of Defense (DoD) Public Key Infrastructure (PKI) Interagency/Partner Interoperability Version 1.0.3 Prepared for: Department of Defense (DoD) PKI August 27, 2008 Page 1 Table of
Recommended operating systems and software for end user services. Operating systems and software not supported for end user services
 Recommended operating systems and software for end user services There are different requirements for different features in Office 365 Beta Beta, but the following list will work with every feature: Windows
Recommended operating systems and software for end user services There are different requirements for different features in Office 365 Beta Beta, but the following list will work with every feature: Windows
Comodo Certification Practice Statement
 Comodo Certification Practice Statement Comodo CA, Ltd. Version 4.0 Effective: 1 July 2012 3rd Floor, Office Village, Exchange Quay, Trafford Road, Salford, Manchester, M5 3EQ, United Kingdom Tel: +44
Comodo Certification Practice Statement Comodo CA, Ltd. Version 4.0 Effective: 1 July 2012 3rd Floor, Office Village, Exchange Quay, Trafford Road, Salford, Manchester, M5 3EQ, United Kingdom Tel: +44
apple WWDR Certification Practice Statement Version 1.8 June 11, 2012 Apple Inc.
 Apple Inc. Certification Authority Certification Practice Statement Worldwide Developer Relations Version 1.8 Effective Date: June 11, 2012 Table of Contents 1. Introduction... 4 1.1. Trademarks... 4 1.2.
Apple Inc. Certification Authority Certification Practice Statement Worldwide Developer Relations Version 1.8 Effective Date: June 11, 2012 Table of Contents 1. Introduction... 4 1.1. Trademarks... 4 1.2.
Access to Front Office services
 Electricity Transmission System Operator Access to Front Office services Supported Configuration Version 1.4, 2009-07-16 Page : 2/5 CONTENT 1. Purpose of the document 3 2. Operating systems supported for
Electricity Transmission System Operator Access to Front Office services Supported Configuration Version 1.4, 2009-07-16 Page : 2/5 CONTENT 1. Purpose of the document 3 2. Operating systems supported for
ENTRUST CLOUD. SSL Digital Certificates, Discovery & Management +1-888-690-2424. entrust@entrust.com entrust.com
 ENTRUST CLOUD SSL Digital Certificates, Discovery & Management +1-888-690-2424 entrust@entrust.com entrust.com Entrust Cloud SSL Digital Certificates, Discovery & Management Digital certificates have emerged
ENTRUST CLOUD SSL Digital Certificates, Discovery & Management +1-888-690-2424 entrust@entrust.com entrust.com Entrust Cloud SSL Digital Certificates, Discovery & Management Digital certificates have emerged
Comodo Extended Validation (EV) Certification Practice Statement
 Comodo Extended Validation (EV) Certification Practice Statement Comodo CA, Ltd. Version 1.03 4th June 2007 3rd Floor, 26 Office Village, Exchange Quay, Trafford Road, Salford, Manchester, M5 3EQ, United
Comodo Extended Validation (EV) Certification Practice Statement Comodo CA, Ltd. Version 1.03 4th June 2007 3rd Floor, 26 Office Village, Exchange Quay, Trafford Road, Salford, Manchester, M5 3EQ, United
How to Setup your E-mail Account -Apple Mail for Mac OS X 1- Open Mail
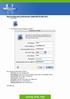 How to Setup your E-mail Account -Apple Mail for Mac OS X 1- Open Mail 2- The welcome screen will appear as follow: Fill in the above information as follow Full Name: type your display name E-Mail address:
How to Setup your E-mail Account -Apple Mail for Mac OS X 1- Open Mail 2- The welcome screen will appear as follow: Fill in the above information as follow Full Name: type your display name E-Mail address:
Internet E-Mail Encryption S/Mime Standard
 Internet E-Mail Encryption S/Mime Standard Disclaimer: Successfully setting up encryption functions in most e-mail clients is usually not a problematic task. However, it should be noted that, when configuring
Internet E-Mail Encryption S/Mime Standard Disclaimer: Successfully setting up encryption functions in most e-mail clients is usually not a problematic task. However, it should be noted that, when configuring
Introduction. About Image-X Enterprises. Overview of PKI Technology
 Digital Signature x Introduction In recent years, use of digital or electronic signatures has rapidly increased in an effort to streamline all types of business transactions. There are two types of electronic
Digital Signature x Introduction In recent years, use of digital or electronic signatures has rapidly increased in an effort to streamline all types of business transactions. There are two types of electronic
Digital certificates and SSL
 Digital certificates and SSL 20 out of 33 rated this helpful Applies to: Exchange Server 2013 Topic Last Modified: 2013-08-26 Secure Sockets Layer (SSL) is a method for securing communications between
Digital certificates and SSL 20 out of 33 rated this helpful Applies to: Exchange Server 2013 Topic Last Modified: 2013-08-26 Secure Sockets Layer (SSL) is a method for securing communications between
Extended Validation (EV) SSL Certificates. Key to Online Success for you and your customers
 Extended Validation (EV) SSL Certificates EV SSL certificates are a new industry standard for identity assurance and authentication A green trust indicator in the web browser illustrates that this website
Extended Validation (EV) SSL Certificates EV SSL certificates are a new industry standard for identity assurance and authentication A green trust indicator in the web browser illustrates that this website
Comodo Certification Practice Statement
 Comodo Certification Practice Statement Notice: This CPS should be read in conjunction with the following documents:- * LiteSSL addendum to the Certificate Practice Statement * Proposed Amendments to the
Comodo Certification Practice Statement Notice: This CPS should be read in conjunction with the following documents:- * LiteSSL addendum to the Certificate Practice Statement * Proposed Amendments to the
Send and receive encrypted e-mails
 Manual Send and receive encrypted e-mails Bank J. Safra Sarasin Ltd Document Owner Security Classification Document Type Bank J. Safra Sarasin Ltd internal and external use Manual Document change history
Manual Send and receive encrypted e-mails Bank J. Safra Sarasin Ltd Document Owner Security Classification Document Type Bank J. Safra Sarasin Ltd internal and external use Manual Document change history
How To Configure Email Using Different Email Clients
 How To Configure Email Using Different Email Clients This document will show step by step instructions for setting up and updating email accounts using different Email Clients. Always remember to verify
How To Configure Email Using Different Email Clients This document will show step by step instructions for setting up and updating email accounts using different Email Clients. Always remember to verify
bank zweiplus email Gateway user manual
 bank zweiplus email Gateway user manual T +41 (0)58 059 22 22, F +41 (0)58 059 22 44, www.bankzweiplus.ch 1/29 Table of contents 1 Foreword... 3 2 Important Notes... 3 2.1 General... 3 2.2 Password...
bank zweiplus email Gateway user manual T +41 (0)58 059 22 22, F +41 (0)58 059 22 44, www.bankzweiplus.ch 1/29 Table of contents 1 Foreword... 3 2 Important Notes... 3 2.1 General... 3 2.2 Password...
Minimum Requirements for Web Based Applications
 Recommended Browsers Skyward recognizes the diverse Operating Systems, Devices, and Internet browsers our customers are using. While we want every customer to have the best possible experience, we recognize
Recommended Browsers Skyward recognizes the diverse Operating Systems, Devices, and Internet browsers our customers are using. While we want every customer to have the best possible experience, we recognize
An Introduction to CODE SIGNING
 An Introduction to CODE SIGNING CONTENTS. 1 What is Code Signing. 03 2 Code Signing Certificates 101...05 3 Why & When to Digitally Sign Code.09 4 Self Signing vs. Publicly Trusted...12 5 Code Signing
An Introduction to CODE SIGNING CONTENTS. 1 What is Code Signing. 03 2 Code Signing Certificates 101...05 3 Why & When to Digitally Sign Code.09 4 Self Signing vs. Publicly Trusted...12 5 Code Signing
SSL Certificates 101
 Whether you are an individual or a company, you should approach online security in the same way that you would approach physical security for your home or business. Not only does it make you feel safer
Whether you are an individual or a company, you should approach online security in the same way that you would approach physical security for your home or business. Not only does it make you feel safer
Gain a New Level of Trust with Extended Validation SSL Certificates
 Gain a New Level of Trust with Extended Validation SSL Certificates Higher Standard for SSL Certificates Malicious Internet activities such as phishing and pharming have victimized millions of people.
Gain a New Level of Trust with Extended Validation SSL Certificates Higher Standard for SSL Certificates Malicious Internet activities such as phishing and pharming have victimized millions of people.
6. Is it mandatory to have the digital certificate issued from NICCA?...3. 7. Is it mandatory for the sender and receiver to have a NIC email id?...
 FAQ FOR S/MIME 1. What is S/MIME?...2 2. What is digital certificate?...2 3. What is an encrypted email?...2 4. Is it mandatory to use this service?...2 5. What I need to do to start using S/MIME service?...2
FAQ FOR S/MIME 1. What is S/MIME?...2 2. What is digital certificate?...2 3. What is an encrypted email?...2 4. Is it mandatory to use this service?...2 5. What I need to do to start using S/MIME service?...2
The DoD Public Key Infrastructure And Public Key-Enabling Frequently Asked Questions
 The DoD Public Key Infrastructure And Public Key-Enabling Frequently Asked Questions May 3, 2004 TABLE OF CONTENTS GENERAL PKI QUESTIONS... 1 1. What is PKI?...1 2. What functionality is provided by a
The DoD Public Key Infrastructure And Public Key-Enabling Frequently Asked Questions May 3, 2004 TABLE OF CONTENTS GENERAL PKI QUESTIONS... 1 1. What is PKI?...1 2. What functionality is provided by a
Basics of SSL Certification
 Introduction To secure transmission of information from browser to a web server, a security protocol is used. SSL (Secure Socket Lock) is one of the most popular and widely accepted security protocols,
Introduction To secure transmission of information from browser to a web server, a security protocol is used. SSL (Secure Socket Lock) is one of the most popular and widely accepted security protocols,
StartCom Certification Authority
 StartCom Certification Authority Intermediate Certification Authority Policy Appendix Version: 1.5 Status: Final Updated: 05/04/11 Copyright: Start Commercial (StartCom) Ltd. Author: Eddy Nigg Introduction
StartCom Certification Authority Intermediate Certification Authority Policy Appendix Version: 1.5 Status: Final Updated: 05/04/11 Copyright: Start Commercial (StartCom) Ltd. Author: Eddy Nigg Introduction
IPv4 Shortage Multiple SSL Certificates on a single IP address
 GlobalSign. A GMO Internet Inc group company. IPv4 Shortage Multiple SSL Certificates on a single IP address Paul van Brouwershaven EMEA Business Development Director GLOBALSIGN SOLUTIONS Visible Trust
GlobalSign. A GMO Internet Inc group company. IPv4 Shortage Multiple SSL Certificates on a single IP address Paul van Brouwershaven EMEA Business Development Director GLOBALSIGN SOLUTIONS Visible Trust
Configuration Manual for Lime Domains
 Email Accounts Configuration Manual for Lime Domains Table of Contents Introduction:... 2 To configure your Outlook Express client:... 3 To configure your Microsoft Outlook client:... 12 To configure your
Email Accounts Configuration Manual for Lime Domains Table of Contents Introduction:... 2 To configure your Outlook Express client:... 3 To configure your Microsoft Outlook client:... 12 To configure your
PKI Uncovered. Cisco Press. Andre Karamanian Srinivas Tenneti Francois Dessart. 800 East 96th Street. Indianapolis, IN 46240
 PKI Uncovered Andre Karamanian Srinivas Tenneti Francois Dessart Cisco Press 800 East 96th Street Indianapolis, IN 46240 Contents Introduction XIII Part I Core Concepts Chapter 1 Crypto Refresh 1 Confidentiality,
PKI Uncovered Andre Karamanian Srinivas Tenneti Francois Dessart Cisco Press 800 East 96th Street Indianapolis, IN 46240 Contents Introduction XIII Part I Core Concepts Chapter 1 Crypto Refresh 1 Confidentiality,
Certificates. Noah Zani, Tim Strasser, Andrés Baumeler
 Certificates Noah Zani, Tim Strasser, Andrés Baumeler Overview Motivation Introduction Public Key Infrastructure (PKI) Economic Aspects Motivation Need for secure, trusted communication Growing certificate
Certificates Noah Zani, Tim Strasser, Andrés Baumeler Overview Motivation Introduction Public Key Infrastructure (PKI) Economic Aspects Motivation Need for secure, trusted communication Growing certificate
Web Hosting. E-Mail Hosting. Cloud File Hosting. The Genio Group (214) 732-7411 info@thegeniogroup.com www.thegeniogroup.com
 Web Hosting E-Mail Hosting Cloud File Hosting Genio Hosting Servers All of Genio s Hosting Servers run on Apple hardware running Mac OS X Server. Mac OS X Server leverages the computing power of 64-bit
Web Hosting E-Mail Hosting Cloud File Hosting Genio Hosting Servers All of Genio s Hosting Servers run on Apple hardware running Mac OS X Server. Mac OS X Server leverages the computing power of 64-bit
The Joys of Importing & Using an S/MIME Certificate CCIT Publication
 The Joys of Importing & Using an S/MIME Certificate CCIT Publication The Joys of Importing & Using an S/MIME Certificate Page 1 / 24 Table of Contents The Joys of Importing & Using an S/MIME Certificate...3
The Joys of Importing & Using an S/MIME Certificate CCIT Publication The Joys of Importing & Using an S/MIME Certificate Page 1 / 24 Table of Contents The Joys of Importing & Using an S/MIME Certificate...3
This manual will help you connect your Microsoft Windows XP, Vista, or 7, or Apple OS X computer to the University of Maryland campus data network.
 This manual will help you connect your Microsoft Windows XP, Vista, or 7, or Apple OS X computer to the University of Maryland campus data network. Prerequisites for Network Registration: 1. In order to
This manual will help you connect your Microsoft Windows XP, Vista, or 7, or Apple OS X computer to the University of Maryland campus data network. Prerequisites for Network Registration: 1. In order to
Digital Certificates (Public Key Infrastructure) Reshma Afshar Indiana State University
 Digital Certificates (Public Key Infrastructure) Reshma Afshar Indiana State University October 2015 1 List of Figures Contents 1 Introduction 1 2 History 2 3 Public Key Infrastructure (PKI) 3 3.1 Certificate
Digital Certificates (Public Key Infrastructure) Reshma Afshar Indiana State University October 2015 1 List of Figures Contents 1 Introduction 1 2 History 2 3 Public Key Infrastructure (PKI) 3 3.1 Certificate
Securing Service Access with Digital Certificates
 Securing Service Access with Digital Certificates Jovana Palibrk, AMRES NA3 T2, Tbilisi, December 2013. Agenda Theory Cryptographic Protocols and Techniques Public Key Infrastructure TERENA Certificate
Securing Service Access with Digital Certificates Jovana Palibrk, AMRES NA3 T2, Tbilisi, December 2013. Agenda Theory Cryptographic Protocols and Techniques Public Key Infrastructure TERENA Certificate
thawte Certification Practice Statement Version 2.3
 thawte Certification Practice Statement Version 2.3 Effective Date: July, 2006 thawte Certification Practice Statement 2006 thawte, Inc. All rights reserved. Printed in the United States of America. Revision
thawte Certification Practice Statement Version 2.3 Effective Date: July, 2006 thawte Certification Practice Statement 2006 thawte, Inc. All rights reserved. Printed in the United States of America. Revision
BEGINNERS GUIDE BEGINNERS GUIDE TO SSL CERTIFICATES: MAKING THE BEST CHOICE WHEN CONSIDERING YOUR ONLINE SECURITY OPTIONS
 BEGINNERS GUIDE TO SSL CERTIFICATES: MAKING THE BEST CHOICE WHEN CONSIDERING YOUR ONLINE SECURITY OPTIONS BEGINNERS GUIDE TO SSL CERTIFICATES INTRODUCTION Whether you are an individual or a company, you
BEGINNERS GUIDE TO SSL CERTIFICATES: MAKING THE BEST CHOICE WHEN CONSIDERING YOUR ONLINE SECURITY OPTIONS BEGINNERS GUIDE TO SSL CERTIFICATES INTRODUCTION Whether you are an individual or a company, you
BEGINNER S GUIDE TO SSL CERTIFICATES: Making the best choice when considering your online security options
 BEGINNER S GUIDE TO SSL CERTIFICATES: Making the best choice when considering your online security options BEGINNERS GUIDE TO SSL CERTIFICATES Introduction Whether you are an individual or a company, you
BEGINNER S GUIDE TO SSL CERTIFICATES: Making the best choice when considering your online security options BEGINNERS GUIDE TO SSL CERTIFICATES Introduction Whether you are an individual or a company, you
ETSI SR 003 091 V1.1.2 (2013-03)
 SR 003 091 V1.1.2 (2013-03) Special Report Electronic Signatures and Infrastructures (ESI); Recommendations on Governance and Audit Regime for CAB Forum Extended Validation and Baseline Certificates 2
SR 003 091 V1.1.2 (2013-03) Special Report Electronic Signatures and Infrastructures (ESI); Recommendations on Governance and Audit Regime for CAB Forum Extended Validation and Baseline Certificates 2
Software as a Service (SaaS) Requirements
 Introduction Software as a Service (SaaS) Requirements Software as a Service (SaaS) is a software service model where an application is hosted as a service provided to customers across the Internet. By
Introduction Software as a Service (SaaS) Requirements Software as a Service (SaaS) is a software service model where an application is hosted as a service provided to customers across the Internet. By
Division of Information Technology Lehman College CUNY
 Division of Information Technology Lehman College CUNY Using Lehman s Secure Outgoing (SMTP) Server Updated April 16, 2013 Are you able to receive your Lehman email on your smart phone, laptop or tablet
Division of Information Technology Lehman College CUNY Using Lehman s Secure Outgoing (SMTP) Server Updated April 16, 2013 Are you able to receive your Lehman email on your smart phone, laptop or tablet
Exchange (UCMAIL) Configuration Procedures
 Exchange (UCMAIL) Configuration Procedures Last Updated: 09/04/2008 by Jon Adams, UCit Email Services Table of Contents New Features for Exchange 2007... 2 Supported Mail Clients... 3 Unsupported or Incompatible
Exchange (UCMAIL) Configuration Procedures Last Updated: 09/04/2008 by Jon Adams, UCit Email Services Table of Contents New Features for Exchange 2007... 2 Supported Mail Clients... 3 Unsupported or Incompatible
The IceWarp SSL Certificate Process
 IceWarp Unified Communications The IceWarp SSL Certificate Process Version 10.3 Printed on 26 November, 2010 Contents The IceWarp SSL Certificate Process 1 Choosing the Proper Certificate Type... 2 Creating
IceWarp Unified Communications The IceWarp SSL Certificate Process Version 10.3 Printed on 26 November, 2010 Contents The IceWarp SSL Certificate Process 1 Choosing the Proper Certificate Type... 2 Creating
ESnet SSL CA service Certificate Policy And Certification Practice Statement Version 1.0
 ESnet SSL CA service Certificate Policy And Certification Practice Statement Version 1.0 June 30, 2004 Table of Contents Table of Contents...2 1 Introduction...3 1.1 Overview...3 1.1.1 General Definitions...4
ESnet SSL CA service Certificate Policy And Certification Practice Statement Version 1.0 June 30, 2004 Table of Contents Table of Contents...2 1 Introduction...3 1.1 Overview...3 1.1.1 General Definitions...4
National Certification Authority Framework in Sri Lanka
 National Certification Authority Framework in Sri Lanka By Rohana Palliyaguru Manager Operations & Principal Information Security Engineer What is digital Signature? According to UNCITRAL Text 25. Digital
National Certification Authority Framework in Sri Lanka By Rohana Palliyaguru Manager Operations & Principal Information Security Engineer What is digital Signature? According to UNCITRAL Text 25. Digital
IceWarp SSL Certificate Process
 IceWarp Unified Communications IceWarp SSL Certificate Process Version 10.4 Printed on 26 June, 2012 Contents IceWarp SSL Certificate Process 1 Choosing the Proper Certificate Type... 2 Creating your
IceWarp Unified Communications IceWarp SSL Certificate Process Version 10.4 Printed on 26 June, 2012 Contents IceWarp SSL Certificate Process 1 Choosing the Proper Certificate Type... 2 Creating your
Extended SSL Certificates
 Introduction Widespread usage of internet has led to the growth of awareness amongst users, who now associate green address bar with security. Though people are able to recognize the green bar, there is
Introduction Widespread usage of internet has led to the growth of awareness amongst users, who now associate green address bar with security. Though people are able to recognize the green bar, there is
Industry Leading Encryption Balanced Offerings from domain validated to secure EV certificates Mobile Device Capability Full Service and Support
 Be the Trusted Security Provider Our Customers Need The demand for online security products is greater than ever due in part to the prevalence of cybercrime in the news headlines. Given the nature of their
Be the Trusted Security Provider Our Customers Need The demand for online security products is greater than ever due in part to the prevalence of cybercrime in the news headlines. Given the nature of their
Djigzo email encryption. Djigzo white paper
 Djigzo email encryption Djigzo white paper Copyright 2009-2011, djigzo.com. Introduction Most email is sent as plain text. This means that anyone who can intercept email messages, either in transit or
Djigzo email encryption Djigzo white paper Copyright 2009-2011, djigzo.com. Introduction Most email is sent as plain text. This means that anyone who can intercept email messages, either in transit or
PrivaSphere Gateway Certificate Authority (GW CA)
 PrivaSphere Gateway Certificate Authority (GW CA) Send and receive secure emails with your email program through restricting firewalls using SMIME gateway functionalities. PrivaSphere Secure Messaging
PrivaSphere Gateway Certificate Authority (GW CA) Send and receive secure emails with your email program through restricting firewalls using SMIME gateway functionalities. PrivaSphere Secure Messaging
CSC E Mail. Mobile Device Configuration Settings and Setup Instructions
 CSC E Mail Mobile Device Configuration Settings and Setup Instructions Contents Overview... 3 Android (Droid, Google Android, etc.)... 4 Exchange Settings... 4... 4 RIM Blackberry... 5... 5 Apple iphone
CSC E Mail Mobile Device Configuration Settings and Setup Instructions Contents Overview... 3 Android (Droid, Google Android, etc.)... 4 Exchange Settings... 4... 4 RIM Blackberry... 5... 5 Apple iphone
SafeNet Authentication Client (Mac)
 SafeNet Authentication Client (Mac) Version 8.2 SP2 Revision A Administrator s Guide 1 Copyright 2014 SafeNet, Inc. All rights reserved. All attempts have been made to make the information in this document
SafeNet Authentication Client (Mac) Version 8.2 SP2 Revision A Administrator s Guide 1 Copyright 2014 SafeNet, Inc. All rights reserved. All attempts have been made to make the information in this document
Microsoft Trusted Root Certificate: Program Requirements
 Microsoft Trusted Root Certificate: Program Requirements 1. Introduction The Microsoft Root Certificate Program supports the distribution of root certificates, enabling customers to trust Windows products.
Microsoft Trusted Root Certificate: Program Requirements 1. Introduction The Microsoft Root Certificate Program supports the distribution of root certificates, enabling customers to trust Windows products.
CHARTER BUSINESS custom hosting faqs 2010 INTERNET. Q. How do I access my email? Q. How do I change or reset a password for an email account?
 Contents Page Q. How do I access my email? Q. How do I change or reset a password for an email account? Q. How do I forward or redirect my messages to a different email address? Q. How do I set up an auto-reply
Contents Page Q. How do I access my email? Q. How do I change or reset a password for an email account? Q. How do I forward or redirect my messages to a different email address? Q. How do I set up an auto-reply
ICE Trade Vault. Public User & Technology Guide June 6, 2014
 ICE Trade Vault Public User & Technology Guide June 6, 2014 This material may not be reproduced or redistributed in whole or in part without the express, prior written consent of IntercontinentalExchange,
ICE Trade Vault Public User & Technology Guide June 6, 2014 This material may not be reproduced or redistributed in whole or in part without the express, prior written consent of IntercontinentalExchange,
Personal Secure Email Certificate
 Entrust Certificate Services Personal Secure Email Certificate Enrollment Guide Date of Issue: October 2010 Copyright 2010 Entrust. All rights reserved. Entrust is a trademark or a registered trademark
Entrust Certificate Services Personal Secure Email Certificate Enrollment Guide Date of Issue: October 2010 Copyright 2010 Entrust. All rights reserved. Entrust is a trademark or a registered trademark
A Proper Foundation: Extended Validation SSL
 A Proper Foundation: Extended Validation SSL A critical model for SSL digital certificates and browser trust Get this White Paper Entrust, Inc. All Rights Reserved. 1 1 Contents Context of Internet Security...
A Proper Foundation: Extended Validation SSL A critical model for SSL digital certificates and browser trust Get this White Paper Entrust, Inc. All Rights Reserved. 1 1 Contents Context of Internet Security...
PKI Contacts PKI for Fraunhofer Contacts
 Fraunhofer Competence Center PKI PKI Contacts PKI for Fraunhofer Contacts User manual for communication partners of the Fraunhofer-Gesellschaft Author[s]: Uwe Bendisch, Maximilian Gottwald As at: 15.10.2013
Fraunhofer Competence Center PKI PKI Contacts PKI for Fraunhofer Contacts User manual for communication partners of the Fraunhofer-Gesellschaft Author[s]: Uwe Bendisch, Maximilian Gottwald As at: 15.10.2013
beginners guide Beginners Guide Certificates the best decision when considering your online security options.
 Beginners Guide to Digital SSL Certificates the best decision when considering your online security options. Beginners Guide to Digital SSL Certificates introduction Whether you are an individual or a
Beginners Guide to Digital SSL Certificates the best decision when considering your online security options. Beginners Guide to Digital SSL Certificates introduction Whether you are an individual or a
Certificate Policy and Certification Practice Statement CNRS/CNRS-Projets/Datagrid-fr
 Certificate Policy and Certification Practice Statement CNRS/CNRS-Projets/Datagrid-fr Version 0.3 August 2002 Online : http://www.urec.cnrs.fr/igc/doc/datagrid-fr.policy.pdf Old versions Version 0.2 :
Certificate Policy and Certification Practice Statement CNRS/CNRS-Projets/Datagrid-fr Version 0.3 August 2002 Online : http://www.urec.cnrs.fr/igc/doc/datagrid-fr.policy.pdf Old versions Version 0.2 :
Comodo Extended Validation (EV) Certification Practice Statement
 Comodo Extended Validation (EV) Certification Practice Statement Comodo CA, Ltd. Version 1.0 8 December 2006 3rd Floor, 26 Office Village, Exchange Quay, Trafford Road, Salford, Manchester, M5 3EQ, United
Comodo Extended Validation (EV) Certification Practice Statement Comodo CA, Ltd. Version 1.0 8 December 2006 3rd Floor, 26 Office Village, Exchange Quay, Trafford Road, Salford, Manchester, M5 3EQ, United
Creating Trust Online TM. Identity & Trust Assurance in a changing standards environment. *(Extended Validation)
 Creating Trust Online TM Identity & Trust Assurance in a changing standards environment. *(Extended Validation) Introduction Today, online commerce is worth an estimated US $1 trillion and continues to
Creating Trust Online TM Identity & Trust Assurance in a changing standards environment. *(Extended Validation) Introduction Today, online commerce is worth an estimated US $1 trillion and continues to
Enterprise SSL FEATURES & BENEFITS
 Enterprise SSL FEATURES & BENEFITS What s included: - Powerful 1024-bit signed RSA certificates - Centralised, web-based administrative portal for certificate management - Dynamically-generated site seal
Enterprise SSL FEATURES & BENEFITS What s included: - Powerful 1024-bit signed RSA certificates - Centralised, web-based administrative portal for certificate management - Dynamically-generated site seal
Configuring Your email Client
 Configuring Your email Client Introduction Until last academic year, the University email systems used no data encryption during email transfers to and from the servers. This was very fast but resulted
Configuring Your email Client Introduction Until last academic year, the University email systems used no data encryption during email transfers to and from the servers. This was very fast but resulted
Cisco is a registered trademark or trademark of Cisco Systems, Inc. and/or its affiliates in the United States and certain other countries.
 Legal Notices Copyright 1999, 2009 BMC Software, Inc. Copyright 1996-2014 Numara Software, Inc. BMC, BMC Software, and the BMC Software logo are the exclusive properties of BMC Software, Inc., are registered
Legal Notices Copyright 1999, 2009 BMC Software, Inc. Copyright 1996-2014 Numara Software, Inc. BMC, BMC Software, and the BMC Software logo are the exclusive properties of BMC Software, Inc., are registered
Shaw Secure Powered by McAfee Registration and Installation
 OVERVIEW This document will guide you through the process of account registration, downloading, and installing Shaw Secure Powered by McAfee. If you experience any challenges with the software installation
OVERVIEW This document will guide you through the process of account registration, downloading, and installing Shaw Secure Powered by McAfee. If you experience any challenges with the software installation
DJIGZO EMAIL ENCRYPTION. Djigzo white paper
 DJIGZO EMAIL ENCRYPTION Djigzo white paper Copyright 2009-2011, djigzo.com. Introduction Most email is sent as plain text. This means that anyone who can intercept email messages, either in transit or
DJIGZO EMAIL ENCRYPTION Djigzo white paper Copyright 2009-2011, djigzo.com. Introduction Most email is sent as plain text. This means that anyone who can intercept email messages, either in transit or
Exchanging Medical Records Online with Direct
 Exchanging Medical Records Online with Direct Scott Rea, VP GOV/EDU Relations & Sr. PKI Architect, DigiCert, Inc. sales@digicert.com www.digicert.com +1 (801) 877-2100 Exchanging Medical Records Online
Exchanging Medical Records Online with Direct Scott Rea, VP GOV/EDU Relations & Sr. PKI Architect, DigiCert, Inc. sales@digicert.com www.digicert.com +1 (801) 877-2100 Exchanging Medical Records Online
Djigzo S/MIME setup guide
 Author: Martijn Brinkers Table of Contents...1 Introduction...3 Quick setup...4 Create a CA...4 Fill in the form:...5 Add certificates for internal users...5 Add certificates for external recipients...7
Author: Martijn Brinkers Table of Contents...1 Introduction...3 Quick setup...4 Create a CA...4 Fill in the form:...5 Add certificates for internal users...5 Add certificates for external recipients...7
HOW WILL I KNOW THAT I SHOULD USE THE IAS EMAIL CONTINUITY SERVICE? https://web.ias.edu/updateme/
 WHEN DO I NEED TO ACCESS THE IAS EMAIL CONTINUITY SERVICE? This service is provided to address the following actions during periods where the IAS email servers are offline: 1. If you need to check for
WHEN DO I NEED TO ACCESS THE IAS EMAIL CONTINUITY SERVICE? This service is provided to address the following actions during periods where the IAS email servers are offline: 1. If you need to check for
ITL BULLETIN FOR JULY 2012. Preparing for and Responding to Certification Authority Compromise and Fraudulent Certificate Issuance
 ITL BULLETIN FOR JULY 2012 Preparing for and Responding to Certification Authority Compromise and Fraudulent Certificate Issuance Paul Turner, Venafi William Polk, Computer Security Division, Information
ITL BULLETIN FOR JULY 2012 Preparing for and Responding to Certification Authority Compromise and Fraudulent Certificate Issuance Paul Turner, Venafi William Polk, Computer Security Division, Information
PKI: Public Key Infrastructure
 PKI: Public Key Infrastructure What is it, and why should I care? Conference on Higher Education Computing in Kansas June 3, 2004 Wes Hubert Information Services The University of Kansas Why? PKI adoption
PKI: Public Key Infrastructure What is it, and why should I care? Conference on Higher Education Computing in Kansas June 3, 2004 Wes Hubert Information Services The University of Kansas Why? PKI adoption
SCS: the new Server Certificate Service offering from SWITCH/TERENA
 SCS: the new Server Certificate Service offering from SWITCH/TERENA Kaspar Brand SWITCH 2006 SWITCH A very brief SCS project history Discussions with other European NRENs started in 2004, within TERENA
SCS: the new Server Certificate Service offering from SWITCH/TERENA Kaspar Brand SWITCH 2006 SWITCH A very brief SCS project history Discussions with other European NRENs started in 2004, within TERENA
Beginner s Guide to SSL Certificates
 WHITE PAPER: BEGINNER S GUIDE TO SSL CERTIFICATES White Paper Beginner s Guide to SSL Certificates Making the Best Choice When Considering Your Online Security Options Beginner s Guide to SSL Certificates
WHITE PAPER: BEGINNER S GUIDE TO SSL CERTIFICATES White Paper Beginner s Guide to SSL Certificates Making the Best Choice When Considering Your Online Security Options Beginner s Guide to SSL Certificates
Lepide Active Directory Self Service. Configuration Guide. Follow the simple steps given in this document to start working with
 Lepide Active Directory Self Service Configuration Guide 2014 Follow the simple steps given in this document to start working with Lepide Active Directory Self Service Table of Contents 1. Introduction...3
Lepide Active Directory Self Service Configuration Guide 2014 Follow the simple steps given in this document to start working with Lepide Active Directory Self Service Table of Contents 1. Introduction...3
NetSure Certificate means any of the types of Certificates that are subject to this Plan, as listed in Appendix A, List of Covered Services.
 THIS EXTENDED WARRANTY PROTECTION PLAN ( Plan ) is provided by Symantec Corporation ( Symantec ) to NetSure Subscribers identified below. NetSure Subscribers holding Symantec Trust Network, Thawte, GeoTrust,
THIS EXTENDED WARRANTY PROTECTION PLAN ( Plan ) is provided by Symantec Corporation ( Symantec ) to NetSure Subscribers identified below. NetSure Subscribers holding Symantec Trust Network, Thawte, GeoTrust,
Instructions for Configuring Your Browser Settings and Online Security FAQ s. ios8 Settings for iphone and ipad app
 Instructions for Configuring Your Browser Settings and Online Security FAQ s ios8 Settings for iphone and ipad app General Settings The following browser settings and plug-ins are required to properly
Instructions for Configuring Your Browser Settings and Online Security FAQ s ios8 Settings for iphone and ipad app General Settings The following browser settings and plug-ins are required to properly
Lecture 13. Public Key Distribution (certification) PK-based Needham-Schroeder TTP. 3. [N a, A] PKb 6. [N a, N b ] PKa. 7.
![Lecture 13. Public Key Distribution (certification) PK-based Needham-Schroeder TTP. 3. [N a, A] PKb 6. [N a, N b ] PKa. 7. Lecture 13. Public Key Distribution (certification) PK-based Needham-Schroeder TTP. 3. [N a, A] PKb 6. [N a, N b ] PKa. 7.](/thumbs/29/13269044.jpg) Lecture 13 Public Key Distribution (certification) 1 PK-based Needham-Schroeder TTP 1. A, B 4. B, A 2. {PKb, B}SKT B}SKs 5. {PK a, A} SKT SKs A 3. [N a, A] PKb 6. [N a, N b ] PKa 7. [N b ] PKb B Here,
Lecture 13 Public Key Distribution (certification) 1 PK-based Needham-Schroeder TTP 1. A, B 4. B, A 2. {PKb, B}SKT B}SKs 5. {PK a, A} SKT SKs A 3. [N a, A] PKb 6. [N a, N b ] PKa 7. [N b ] PKb B Here,
GlobalSign Integration Guide
 GlobalSign Integration Guide GlobalSign Enterprise PKI (EPKI) and AirWatch Enterprise MDM 1 v.1.1 Table of Contents Table of Contents... 2 Introduction... 3 GlobalSign Enterprise PKI (EPKI)... 3 Partner
GlobalSign Integration Guide GlobalSign Enterprise PKI (EPKI) and AirWatch Enterprise MDM 1 v.1.1 Table of Contents Table of Contents... 2 Introduction... 3 GlobalSign Enterprise PKI (EPKI)... 3 Partner
Migration Instructions:
 University IT will be moving Exchange email accounts to the University s new mail servers during the month of April 2008. The new mail servers have been built to provide greater redundancy, stronger performance,
University IT will be moving Exchange email accounts to the University s new mail servers during the month of April 2008. The new mail servers have been built to provide greater redundancy, stronger performance,
Managing CA-Signed Certificates
 Managing CA-Signed Certificates T.Rob Wyatt, IoPT Consulting t.rob@ioptconsulting.com Managing CA Certificates for MQ - Intermediate So you want to enable SSL on your MQ channels using a commercial Certificate
Managing CA-Signed Certificates T.Rob Wyatt, IoPT Consulting t.rob@ioptconsulting.com Managing CA Certificates for MQ - Intermediate So you want to enable SSL on your MQ channels using a commercial Certificate
CIPHERMAIL EMAIL ENCRYPTION. CipherMail white paper
 CIPHERMAIL EMAIL ENCRYPTION CipherMail white paper Copyright 2009-2014, ciphermail.com. Introduction Most email is sent as plain text. This means that anyone who can intercept email messages, either in
CIPHERMAIL EMAIL ENCRYPTION CipherMail white paper Copyright 2009-2014, ciphermail.com. Introduction Most email is sent as plain text. This means that anyone who can intercept email messages, either in
How to Disable Common Pop-Up Blockers
 How to Disable Common Pop-Up Blockers Listed below are some of the most popular pop-up blocking software packages, and instructions to enable pop-up windows with them. Pop-up windows must be enabled to
How to Disable Common Pop-Up Blockers Listed below are some of the most popular pop-up blocking software packages, and instructions to enable pop-up windows with them. Pop-up windows must be enabled to
Siemens PKI Certificate Authority (CA) Hierarchy
 Siemens PKI Certificate Authority (CA) Hierarchy Status July 2011 Siemens PKI CA Hierarchy Overview (1) Public Root (available in common OS / Browsers) Baltimore CyberTrust Root (Verizon) Siemens Trust
Siemens PKI Certificate Authority (CA) Hierarchy Status July 2011 Siemens PKI CA Hierarchy Overview (1) Public Root (available in common OS / Browsers) Baltimore CyberTrust Root (Verizon) Siemens Trust
