T Safety Critical Systems Case Study 2: B Method - Basic Concepts
|
|
|
- Roland O’Brien’
- 8 years ago
- Views:
Transcription
1 T Safety Critical Systems Case Study 2: B Method - Basic Concepts February 21, 2008
2 T : Case Study 2: B Method - Basic Concepts 2-1 B method - what is it about? B method describes entities called abstract machines. What is an abstract machine? An example machine would look something like this: MACHINE... VARIABLES... INVARIANT... INITIALISATION... OPERATIONS... END Let s go through each of the constituent parts in the following, together with an example.
3 T : Case Study 2: B Method - Basic Concepts 2-2 MACHINE The MACHINE keyword gives a name to the specification we are currently modelling. It is possible to include MACHINEs from other MACHINEs, so they can be used as building blocks. For a ticketing system we may define: MACHINE Ticket
4 T : Case Study 2: B Method - Basic Concepts 2-3 VARIABLES The VARIABLES keyword is used for introducing variables that define the local state of the system. In this section only the names are given, types are defined later. For a ticketing system we might have two variables: serve and next VARIABLES serve, next
5 T : Case Study 2: B Method - Basic Concepts 2-4 INVARIANT The INVARIANT keyword is used for few purposes. The types for variables are defined here, as well as a statement that is to be true for the variables in all system states. In a sense, INVARIANT is an assertion which causes the execution of a machine to stop if it is violated. For a ticketing system, we may define: INVARIANT serve N next N serve next
6 T : Case Study 2: B Method - Basic Concepts 2-5 OPERATIONS The OPERATIONS keyword defines the interface between the user and the machine. Output are used to communicate results to users, and these are separate from machine s own variables. Preconditions control whether an operation is executed at all. out puts name(inputs) An example of an operation in B is: ss serve next = PRE serve < next THEN ss, serve := serve+1, serve+1 END
7 T : Case Study 2: B Method - Basic Concepts 2-6 INITIALISATION The INITIALISATIONS part of a machine gives the initial state of the machine. variable defined in the VARIABLES section must be given some value. Each In our Ticketing machine, we may define: INITIALISATION serve, next := 0, 0
8 T : Case Study 2: B Method - Basic Concepts 2-7 My first complete B machine... MACHINE Ticket VARIABLES serve, next INVARIANT serve N next N serve next INITIALISATION serve, next := 0, 0 OPERATIONS ss serve next = PRE serve < next THEN ss, serve := serve + 1, serve + 1 END ; tt take ticket = PRE true THEN tt, next := next, next + 1 END END
9 T : Case Study 2: B Method - Basic Concepts 2-8 Couple points about sets... As a little refresher on sets, let s do the following questions (here, card refers to set cardinality, and P is the notation for powerset): Assume that we have MEMBER = { f red, ginger, harold}. Compute the following: 1. P MEMBER 2. MEMBER MEMBER 3. card(p(member MEMBER)) 4. card(pp MEMBER) You should have set cardinalities of 8, 9, 512 and 256 for your answers, respectively...
10 T : Case Study 2: B Method - Basic Concepts 2-9 Little hint on Quantified Logic You are already familiar with this logic, but the only point worth mentioning is the duality of universal and existential quantification. So, here you go: x.(x T P) = x.(x T P) x.(x T P) = x.(x T P)
11 T : Case Study 2: B Method - Basic Concepts 2-10 Substitutions.. B method makes heavy use of substitutions, so let s study it in more detail. P[E/x] is the same as expression P except that E is substituted for every occurrence of x. Examples: (x < y)[(x+y+z)/y] = (x < x+y+z) (serve < next next < last 4)[serve+1/serve] = serve+1 < next next < last 4 (members PERSON)[members {new}/members] = members {new} PERSON
12 T : Case Study 2: B Method - Basic Concepts 2-11 Hints on Substitutions... Couple things are worth mentioning about Substitutions when we have quantified logic: 1. Re-name bound variables before substitution, if there is a name clash. ( n.(n N n > limit))[n+3/limit] = ( q.(q N q > limit))[n+3/limit] = ( q.(q N q > n+3)) 2. Bound variables are not substituted: ( n.(n N n > limit))[over/n] = ( m.(m N m > limit))[over/n] = ( m.(m N m > limit))
13 T : Case Study 2: B Method - Basic Concepts 2-12 Weakest Preconditions Changes of state happen through transformations, which are caused by operations. Sometimes we know the desired outcome of an operation, and the operation to be executed but are unsure of what preconditions will guarantee the desired outcome to occur. For this purpose, we introduce the concept of Weakest Precondition, which is written as [S]P. P is a logical statement for the desired outcome, S is the operation to be carried out, and [S]P is a logical statement describing the initial states that guarantee P after executing S.
14 T : Case Study 2: B Method - Basic Concepts 2-13 Example of a Weakest Precondition calculation Imagine that x,y {0,1,2}, and we have an operation y := max{0,y x}. Now, we are interested in the values for x and y that guarantee that y > 0 after the operation is finished. In mathematical terms, we want to find [y := max{0,y x}](y > 0) Clearly, we see that (x,y) = (0,1), (0,2), (1,2) satisfy the constraint, and thus the weakest precondition in terms of logic is: [y := max{0,y x}](y > 0) = (x = 0 y = 1) (x = 0 y = 2) (x = 1 y = 2)
15 T : Case Study 2: B Method - Basic Concepts 2-14 Laws of [S]P There are three simple rules for weakest preconditions which can be used to simplify statements: [S](P Q) = [S]P [S]Q [S]P [S]Q = [S](P Q) P = Q implies [S]P = [S]Q
16 T : Case Study 2: B Method - Basic Concepts 2-15 Weakest Preconditions and Assignment Statement Weakest Precondition for assignment statements has a simple form, but you have to see an example to see how it really works... [x := E]P = P[E/x] And to see an example, follow along... [serve := serve+1](serve next) serve+1 next serve < next Similarly [colours := colours {blue}](green colours) green colours {blue} green colours
17 T : Case Study 2: B Method - Basic Concepts 2-16 Weakest Preconditions and Multiple Assignment The above rule may be generalized to multiple assignments in a straightforward manner: [x 1,...,x n := E 1,...,E n ]P = P[E 1,...,E n /x 1,...,x n ] Here s an example: [serve, next := serve + 1, next 1](serve next) serve+1 next 1
18 T : Case Study 2: B Method - Basic Concepts 2-17 The easiest B statement you ll ever see... In B, we have a statement which does nothing. The name for it is skip. As you might think, also the weakest precondition rule for this statement is rather simple... [skip]p = P
19 T : Case Study 2: B Method - Basic Concepts 2-18 Weakest Preconditions and Conditional IF/THEN/ELSE is a very popular construct in programming languages, and B has developed a weakest precondition rule for it. [IF E THEN S ELSE T END]P = (E [S]P) ( E [T]P) Let s compute an example: [IF x > 7 THEN x := x 4 ELSE x := x+3 END](x > 12) = (x > 7 [x := x 4](x > 12)) (x 7 [x := x+3](x > 12)) = (x > 7 x 4 > 12) (x 7 x+3 > 12) = (x > 7 x > 16) (x 7 x > 9) = (x > 16)
20 T : Case Study 2: B Method - Basic Concepts 2-19 Weakest Preconditions and Case clause Case-clauses are also used widely in programming languages. Here is the rule for it in B... CASE E OF EITHER e 1 THEN T 1 OR e 2 THEN T 2 OR... OR e n THEN T n ELSE V END P = E = e 1 [T 1 ]P E = e 2 [T 2 ]P... E = e n [T n ]P (E e 1 E e 2... E e n ) [V]P There s a lot of similarity here to a IF/ELSEIF/.../ELSE clause, and construction of an example is straightforward.
21 T : Case Study 2: B Method - Basic Concepts 2-20 Last Easy Rule... Here s the final rule for weakest preconditions. It is customary for some programs to include a BEGIN/END pair in their language, although it often doesn t add much meaning. In weakest precondition terms, such BEGIN/END pairs may be stripped off as follows: [BEGIN S END]P = [S]P
22 T : Case Study 2: B Method - Basic Concepts 2-21 Thank You... You made it to the end... OK, this was our first look at B method, and some mathematical constructs that are useful there. Next time we ll carry on with machine consistency, relations and functions, and we ll start seeing more complicated B specifications.
23 T : Case Study 2: B Method - Basic Concepts 2-22 References The material in this presentation has been obtained from 1. the b-method - an introduction. Steve Schneider. Palgrave, (This book belongs to the cornerstones of computing series by the same publisher)
Software Engineering
 Software Engineering Lecture 04: The B Specification Method Peter Thiemann University of Freiburg, Germany SS 2013 Peter Thiemann (Univ. Freiburg) Software Engineering SWT 1 / 50 The B specification method
Software Engineering Lecture 04: The B Specification Method Peter Thiemann University of Freiburg, Germany SS 2013 Peter Thiemann (Univ. Freiburg) Software Engineering SWT 1 / 50 The B specification method
Lecture # 06 Introducing abstract Machines Saima Zareen
 Lecture # 06 Introducing abstract Machines Saima Zareen Formal Specification of a System Formal Specification describes the System behavior Operations of system Problem with formal specification is large
Lecture # 06 Introducing abstract Machines Saima Zareen Formal Specification of a System Formal Specification describes the System behavior Operations of system Problem with formal specification is large
Chapter 7. Functions and onto. 7.1 Functions
 Chapter 7 Functions and onto This chapter covers functions, including function composition and what it means for a function to be onto. In the process, we ll see what happens when two dissimilar quantifiers
Chapter 7 Functions and onto This chapter covers functions, including function composition and what it means for a function to be onto. In the process, we ll see what happens when two dissimilar quantifiers
Rigorous Software Development CSCI-GA 3033-009
 Rigorous Software Development CSCI-GA 3033-009 Instructor: Thomas Wies Spring 2013 Lecture 11 Semantics of Programming Languages Denotational Semantics Meaning of a program is defined as the mathematical
Rigorous Software Development CSCI-GA 3033-009 Instructor: Thomas Wies Spring 2013 Lecture 11 Semantics of Programming Languages Denotational Semantics Meaning of a program is defined as the mathematical
Formal Engineering for Industrial Software Development
 Shaoying Liu Formal Engineering for Industrial Software Development Using the SOFL Method With 90 Figures and 30 Tables Springer Contents Introduction 1 1.1 Software Life Cycle... 2 1.2 The Problem 4 1.3
Shaoying Liu Formal Engineering for Industrial Software Development Using the SOFL Method With 90 Figures and 30 Tables Springer Contents Introduction 1 1.1 Software Life Cycle... 2 1.2 The Problem 4 1.3
Predicate Logic Review
 Predicate Logic Review UC Berkeley, Philosophy 142, Spring 2016 John MacFarlane 1 Grammar A term is an individual constant or a variable. An individual constant is a lowercase letter from the beginning
Predicate Logic Review UC Berkeley, Philosophy 142, Spring 2016 John MacFarlane 1 Grammar A term is an individual constant or a variable. An individual constant is a lowercase letter from the beginning
How To Improve Software Quality
 Software Qualities Quality Assurance Maintainer Go Documentation Readable Ce Go Design Functionality Ease of use Ease of learning User Reliability Correctness Efficiency Low Cost Portability Increased
Software Qualities Quality Assurance Maintainer Go Documentation Readable Ce Go Design Functionality Ease of use Ease of learning User Reliability Correctness Efficiency Low Cost Portability Increased
COLLEGE ALGEBRA. Paul Dawkins
 COLLEGE ALGEBRA Paul Dawkins Table of Contents Preface... iii Outline... iv Preliminaries... Introduction... Integer Exponents... Rational Exponents... 9 Real Exponents...5 Radicals...6 Polynomials...5
COLLEGE ALGEBRA Paul Dawkins Table of Contents Preface... iii Outline... iv Preliminaries... Introduction... Integer Exponents... Rational Exponents... 9 Real Exponents...5 Radicals...6 Polynomials...5
Mathematics for Computer Science/Software Engineering. Notes for the course MSM1F3 Dr. R. A. Wilson
 Mathematics for Computer Science/Software Engineering Notes for the course MSM1F3 Dr. R. A. Wilson October 1996 Chapter 1 Logic Lecture no. 1. We introduce the concept of a proposition, which is a statement
Mathematics for Computer Science/Software Engineering Notes for the course MSM1F3 Dr. R. A. Wilson October 1996 Chapter 1 Logic Lecture no. 1. We introduce the concept of a proposition, which is a statement
DNA Determines Your Appearance!
 DNA Determines Your Appearance! Summary DNA contains all the information needed to build your body. Did you know that your DNA determines things such as your eye color, hair color, height, and even the
DNA Determines Your Appearance! Summary DNA contains all the information needed to build your body. Did you know that your DNA determines things such as your eye color, hair color, height, and even the
Configuring the Server(s)
 Introduction Configuring the Server(s) IN THIS CHAPTER. Introduction. Overview of Machine Configuration Options. Installing and Configuring FileMaker Server. Testing Your Installation. Hosting Your File.
Introduction Configuring the Server(s) IN THIS CHAPTER. Introduction. Overview of Machine Configuration Options. Installing and Configuring FileMaker Server. Testing Your Installation. Hosting Your File.
IP Subnetting: Practical Subnet Design and Address Determination Example
 IP Subnetting: Practical Subnet Design and Address Determination Example When educators ask students what they consider to be the most confusing aspect in learning about networking, many say that it is
IP Subnetting: Practical Subnet Design and Address Determination Example When educators ask students what they consider to be the most confusing aspect in learning about networking, many say that it is
Software Design. Software Design. Software design is the process that adds implementation details to the requirements.
 Software Design Software Design Software design is the process that adds implementation details to the requirements. It produces a design specification that can be mapped onto a program. It may take several
Software Design Software Design Software design is the process that adds implementation details to the requirements. It produces a design specification that can be mapped onto a program. It may take several
The FOREX Master Plan
 The FOREX Master Plan 1. Introduction First of all I need to say that I did not write this ebook for me, but for each and every one of you. I hope that it will be beneficial for everybody that reads it
The FOREX Master Plan 1. Introduction First of all I need to say that I did not write this ebook for me, but for each and every one of you. I hope that it will be beneficial for everybody that reads it
Checking Spelling and Grammar
 In this chapter Checking spelling and grammar in a document Use automatic spell-checking and correction Using Word s thesaurus Using other languages and custom dictionaries 13 Checking Spelling and Grammar
In this chapter Checking spelling and grammar in a document Use automatic spell-checking and correction Using Word s thesaurus Using other languages and custom dictionaries 13 Checking Spelling and Grammar
Chapter 9. Systems of Linear Equations
 Chapter 9. Systems of Linear Equations 9.1. Solve Systems of Linear Equations by Graphing KYOTE Standards: CR 21; CA 13 In this section we discuss how to solve systems of two linear equations in two variables
Chapter 9. Systems of Linear Equations 9.1. Solve Systems of Linear Equations by Graphing KYOTE Standards: CR 21; CA 13 In this section we discuss how to solve systems of two linear equations in two variables
Probability and Expected Value
 Probability and Expected Value This handout provides an introduction to probability and expected value. Some of you may already be familiar with some of these topics. Probability and expected value are
Probability and Expected Value This handout provides an introduction to probability and expected value. Some of you may already be familiar with some of these topics. Probability and expected value are
An example of a computable
 An example of a computable absolutely normal number Verónica Becher Santiago Figueira Abstract The first example of an absolutely normal number was given by Sierpinski in 96, twenty years before the concept
An example of a computable absolutely normal number Verónica Becher Santiago Figueira Abstract The first example of an absolutely normal number was given by Sierpinski in 96, twenty years before the concept
15.1 Factoring Polynomials
 LESSON 15.1 Factoring Polynomials Use the structure of an expression to identify ways to rewrite it. Also A.SSE.3? ESSENTIAL QUESTION How can you use the greatest common factor to factor polynomials? EXPLORE
LESSON 15.1 Factoring Polynomials Use the structure of an expression to identify ways to rewrite it. Also A.SSE.3? ESSENTIAL QUESTION How can you use the greatest common factor to factor polynomials? EXPLORE
Basic Probability. Probability: The part of Mathematics devoted to quantify uncertainty
 AMS 5 PROBABILITY Basic Probability Probability: The part of Mathematics devoted to quantify uncertainty Frequency Theory Bayesian Theory Game: Playing Backgammon. The chance of getting (6,6) is 1/36.
AMS 5 PROBABILITY Basic Probability Probability: The part of Mathematics devoted to quantify uncertainty Frequency Theory Bayesian Theory Game: Playing Backgammon. The chance of getting (6,6) is 1/36.
VACATION REQUEST USER S MANUAL
 2013 VACATION REQUEST USER S MANUAL Alejandro Aguilar / IT Application Services Martha P. García / HR 3/21/2013 TABLE OF CONTENTS Vacation Request User s Manual INTRODUCTION... 2 REQUIREMENTS... 3 ACCESSING
2013 VACATION REQUEST USER S MANUAL Alejandro Aguilar / IT Application Services Martha P. García / HR 3/21/2013 TABLE OF CONTENTS Vacation Request User s Manual INTRODUCTION... 2 REQUIREMENTS... 3 ACCESSING
Invalidity in Predicate Logic
 Invalidity in Predicate Logic So far we ve got a method for establishing that a predicate logic argument is valid: do a derivation. But we ve got no method for establishing invalidity. In propositional
Invalidity in Predicate Logic So far we ve got a method for establishing that a predicate logic argument is valid: do a derivation. But we ve got no method for establishing invalidity. In propositional
Execution of A Requirement Model in Software Development
 Execution of A Requirement Model in Software Development Wuwei Shen, Mohsen Guizani and Zijiang Yang Dept of Computer Science, Western Michigan University {wwshen,mguizani,zijiang}@cs.wmich.edu Kevin Compton
Execution of A Requirement Model in Software Development Wuwei Shen, Mohsen Guizani and Zijiang Yang Dept of Computer Science, Western Michigan University {wwshen,mguizani,zijiang}@cs.wmich.edu Kevin Compton
A Quick Algebra Review
 1. Simplifying Epressions. Solving Equations 3. Problem Solving 4. Inequalities 5. Absolute Values 6. Linear Equations 7. Systems of Equations 8. Laws of Eponents 9. Quadratics 10. Rationals 11. Radicals
1. Simplifying Epressions. Solving Equations 3. Problem Solving 4. Inequalities 5. Absolute Values 6. Linear Equations 7. Systems of Equations 8. Laws of Eponents 9. Quadratics 10. Rationals 11. Radicals
Linear Programming Notes VII Sensitivity Analysis
 Linear Programming Notes VII Sensitivity Analysis 1 Introduction When you use a mathematical model to describe reality you must make approximations. The world is more complicated than the kinds of optimization
Linear Programming Notes VII Sensitivity Analysis 1 Introduction When you use a mathematical model to describe reality you must make approximations. The world is more complicated than the kinds of optimization
The fundamental question in economics is 2. Consumer Preferences
 A Theory of Consumer Behavior Preliminaries 1. Introduction The fundamental question in economics is 2. Consumer Preferences Given limited resources, how are goods and service allocated? 1 3. Indifference
A Theory of Consumer Behavior Preliminaries 1. Introduction The fundamental question in economics is 2. Consumer Preferences Given limited resources, how are goods and service allocated? 1 3. Indifference
Memory Systems. Static Random Access Memory (SRAM) Cell
 Memory Systems This chapter begins the discussion of memory systems from the implementation of a single bit. The architecture of memory chips is then constructed using arrays of bit implementations coupled
Memory Systems This chapter begins the discussion of memory systems from the implementation of a single bit. The architecture of memory chips is then constructed using arrays of bit implementations coupled
Scheduling Shop Scheduling. Tim Nieberg
 Scheduling Shop Scheduling Tim Nieberg Shop models: General Introduction Remark: Consider non preemptive problems with regular objectives Notation Shop Problems: m machines, n jobs 1,..., n operations
Scheduling Shop Scheduling Tim Nieberg Shop models: General Introduction Remark: Consider non preemptive problems with regular objectives Notation Shop Problems: m machines, n jobs 1,..., n operations
Monomial Factors. Sometimes the expression to be factored is simple enough to be able to use straightforward inspection.
 The Mathematics 11 Competency Test Monomial Factors The first stage of factoring an algebraic expression involves the identification of any factors which are monomials. We will describe the process by
The Mathematics 11 Competency Test Monomial Factors The first stage of factoring an algebraic expression involves the identification of any factors which are monomials. We will describe the process by
Add in Guide for Microsoft Dynamics NAV May 2012
 Add in Guide for Microsoft Dynamics NAV May 2012 Microsoft Dynamics NAV 4 5 Addin Guide This document will guide you through configuration and basic use of Hipin s Microsoft Dynamics NAV addin. Microsoft
Add in Guide for Microsoft Dynamics NAV May 2012 Microsoft Dynamics NAV 4 5 Addin Guide This document will guide you through configuration and basic use of Hipin s Microsoft Dynamics NAV addin. Microsoft
Dedekind s forgotten axiom and why we should teach it (and why we shouldn t teach mathematical induction in our calculus classes)
 Dedekind s forgotten axiom and why we should teach it (and why we shouldn t teach mathematical induction in our calculus classes) by Jim Propp (UMass Lowell) March 14, 2010 1 / 29 Completeness Three common
Dedekind s forgotten axiom and why we should teach it (and why we shouldn t teach mathematical induction in our calculus classes) by Jim Propp (UMass Lowell) March 14, 2010 1 / 29 Completeness Three common
Python Lists and Loops
 WEEK THREE Python Lists and Loops You ve made it to Week 3, well done! Most programs need to keep track of a list (or collection) of things (e.g. names) at one time or another, and this week we ll show
WEEK THREE Python Lists and Loops You ve made it to Week 3, well done! Most programs need to keep track of a list (or collection) of things (e.g. names) at one time or another, and this week we ll show
Home Assignment 4 OCL
 Home Assignment 4 OCL This home assignment is about writing formal specifications using the Object Constraint Language. You will exercise formulating conditions/invariants on domain models that go beyond
Home Assignment 4 OCL This home assignment is about writing formal specifications using the Object Constraint Language. You will exercise formulating conditions/invariants on domain models that go beyond
Formal Languages and Automata Theory - Regular Expressions and Finite Automata -
 Formal Languages and Automata Theory - Regular Expressions and Finite Automata - Samarjit Chakraborty Computer Engineering and Networks Laboratory Swiss Federal Institute of Technology (ETH) Zürich March
Formal Languages and Automata Theory - Regular Expressions and Finite Automata - Samarjit Chakraborty Computer Engineering and Networks Laboratory Swiss Federal Institute of Technology (ETH) Zürich March
Colour by Numbers Image Representation
 Activity 2 Colour by Numbers Image Representation Summary Computers store drawings, photographs and other pictures using only numbers. The following activity demonstrates how they can do this. Curriculum
Activity 2 Colour by Numbers Image Representation Summary Computers store drawings, photographs and other pictures using only numbers. The following activity demonstrates how they can do this. Curriculum
A Framework for the Semantics of Behavioral Contracts
 A Framework for the Semantics of Behavioral Contracts Ashley McNeile Metamaxim Ltd, 48 Brunswick Gardens, London W8 4AN, UK ashley.mcneile@metamaxim.com Abstract. Contracts have proved a powerful concept
A Framework for the Semantics of Behavioral Contracts Ashley McNeile Metamaxim Ltd, 48 Brunswick Gardens, London W8 4AN, UK ashley.mcneile@metamaxim.com Abstract. Contracts have proved a powerful concept
Agent s Handbook. Your guide to satisfied customers
 Agent s Handbook Your guide to satisfied customers Introduction LiveChat is a tool that facilitates communication between a company and its customers. Agents who wield that tool use it to make customers
Agent s Handbook Your guide to satisfied customers Introduction LiveChat is a tool that facilitates communication between a company and its customers. Agents who wield that tool use it to make customers
and forms from multiple folders simultaneously to send out for e signing as the system will automatically create a Queue as you select documents.
 This guide was prepared to show our members how to submit saved forms (and/or uploaded documents) out for e signature using our built in integration with Settleware s secure e signing services. Once you
This guide was prepared to show our members how to submit saved forms (and/or uploaded documents) out for e signature using our built in integration with Settleware s secure e signing services. Once you
Constrained Clustering of Territories in the Context of Car Insurance
 Constrained Clustering of Territories in the Context of Car Insurance Samuel Perreault Jean-Philippe Le Cavalier Laval University July 2014 Perreault & Le Cavalier (ULaval) Constrained Clustering July
Constrained Clustering of Territories in the Context of Car Insurance Samuel Perreault Jean-Philippe Le Cavalier Laval University July 2014 Perreault & Le Cavalier (ULaval) Constrained Clustering July
Introducing Formal Methods. Software Engineering and Formal Methods
 Introducing Formal Methods Formal Methods for Software Specification and Analysis: An Overview 1 Software Engineering and Formal Methods Every Software engineering methodology is based on a recommended
Introducing Formal Methods Formal Methods for Software Specification and Analysis: An Overview 1 Software Engineering and Formal Methods Every Software engineering methodology is based on a recommended
Academic Success Centre
 250) 960-6367 Factoring Polynomials Sometimes when we try to solve or simplify an equation or expression involving polynomials the way that it looks can hinder our progress in finding a solution. Factorization
250) 960-6367 Factoring Polynomials Sometimes when we try to solve or simplify an equation or expression involving polynomials the way that it looks can hinder our progress in finding a solution. Factorization
Chapter 3. Cartesian Products and Relations. 3.1 Cartesian Products
 Chapter 3 Cartesian Products and Relations The material in this chapter is the first real encounter with abstraction. Relations are very general thing they are a special type of subset. After introducing
Chapter 3 Cartesian Products and Relations The material in this chapter is the first real encounter with abstraction. Relations are very general thing they are a special type of subset. After introducing
Application Notes for Configuring Dorado Software Redcell Enterprise Bundle using SNMP with Avaya Communication Manager - Issue 1.
 Avaya Solution & Interoperability Test Lab Application Notes for Configuring Dorado Software Redcell Enterprise Bundle using SNMP with Avaya Communication Manager - Issue 1.0 Abstract These Application
Avaya Solution & Interoperability Test Lab Application Notes for Configuring Dorado Software Redcell Enterprise Bundle using SNMP with Avaya Communication Manager - Issue 1.0 Abstract These Application
An Innocent Investigation
 An Innocent Investigation D. Joyce, Clark University January 2006 The beginning. Have you ever wondered why every number is either even or odd? I don t mean to ask if you ever wondered whether every number
An Innocent Investigation D. Joyce, Clark University January 2006 The beginning. Have you ever wondered why every number is either even or odd? I don t mean to ask if you ever wondered whether every number
US Terms. Rosa. Frida s Flowers Blanket Block 4
 US Terms Rosa Frida s Flowers Blanket Block 4 Block 4 Rosa One of Frida s very first paintings is entitled Still Life Roses and she painted it in 95. Frida often wore roses in her hair or tucked one behind
US Terms Rosa Frida s Flowers Blanket Block 4 Block 4 Rosa One of Frida s very first paintings is entitled Still Life Roses and she painted it in 95. Frida often wore roses in her hair or tucked one behind
Word Problems Involving Systems of Linear Equations
 Word Problems Involving Systems of Linear Equations Many word problems will give rise to systems of equations that is, a pair of equations like this: 2x+3y = 10 x 6y = 5 You can solve a system of equations
Word Problems Involving Systems of Linear Equations Many word problems will give rise to systems of equations that is, a pair of equations like this: 2x+3y = 10 x 6y = 5 You can solve a system of equations
Sudoku puzzles and how to solve them
 Sudoku puzzles and how to solve them Andries E. Brouwer 2006-05-31 1 Sudoku Figure 1: Two puzzles the second one is difficult A Sudoku puzzle (of classical type ) consists of a 9-by-9 matrix partitioned
Sudoku puzzles and how to solve them Andries E. Brouwer 2006-05-31 1 Sudoku Figure 1: Two puzzles the second one is difficult A Sudoku puzzle (of classical type ) consists of a 9-by-9 matrix partitioned
PROPERTECHNIQUEOFSOFTWARE INSPECTIONUSING GUARDED COMMANDLANGUAGE
 International Journal of Computer ScienceandCommunication Vol. 2, No. 1, January-June2011, pp. 153-157 PROPERTECHNIQUEOFSOFTWARE INSPECTIONUSING GUARDED COMMANDLANGUAGE Neeraj Kumar Singhania University,
International Journal of Computer ScienceandCommunication Vol. 2, No. 1, January-June2011, pp. 153-157 PROPERTECHNIQUEOFSOFTWARE INSPECTIONUSING GUARDED COMMANDLANGUAGE Neeraj Kumar Singhania University,
A Concrete Introduction. to the Abstract Concepts. of Integers and Algebra using Algebra Tiles
 A Concrete Introduction to the Abstract Concepts of Integers and Algebra using Algebra Tiles Table of Contents Introduction... 1 page Integers 1: Introduction to Integers... 3 2: Working with Algebra Tiles...
A Concrete Introduction to the Abstract Concepts of Integers and Algebra using Algebra Tiles Table of Contents Introduction... 1 page Integers 1: Introduction to Integers... 3 2: Working with Algebra Tiles...
Copyrighted Material. Chapter 1 DEGREE OF A CURVE
 Chapter 1 DEGREE OF A CURVE Road Map The idea of degree is a fundamental concept, which will take us several chapters to explore in depth. We begin by explaining what an algebraic curve is, and offer two
Chapter 1 DEGREE OF A CURVE Road Map The idea of degree is a fundamental concept, which will take us several chapters to explore in depth. We begin by explaining what an algebraic curve is, and offer two
Double Deck Blackjack
 Double Deck Blackjack Double Deck Blackjack is far more volatile than Multi Deck for the following reasons; The Running & True Card Counts can swing drastically from one Round to the next So few cards
Double Deck Blackjack Double Deck Blackjack is far more volatile than Multi Deck for the following reasons; The Running & True Card Counts can swing drastically from one Round to the next So few cards
[Refer Slide Time: 05:10]
![[Refer Slide Time: 05:10] [Refer Slide Time: 05:10]](/thumbs/29/13447118.jpg) Principles of Programming Languages Prof: S. Arun Kumar Department of Computer Science and Engineering Indian Institute of Technology Delhi Lecture no 7 Lecture Title: Syntactic Classes Welcome to lecture
Principles of Programming Languages Prof: S. Arun Kumar Department of Computer Science and Engineering Indian Institute of Technology Delhi Lecture no 7 Lecture Title: Syntactic Classes Welcome to lecture
Capturing Database Transformations for Big Data Analytics
 Capturing Database Transformations for Big Data Analytics David Sergio Matusevich University of Houston Organization Introduction Classification Program Case Study Conclusions Extending ER Models to Capture
Capturing Database Transformations for Big Data Analytics David Sergio Matusevich University of Houston Organization Introduction Classification Program Case Study Conclusions Extending ER Models to Capture
WORKING IN TEAMS WITH CASECOMPLETE AND MICROSOFT VISUAL SOURCE SAFE. Contents
 WORKING IN TEAMS WITH CASECOMPLETE AND MICROSOFT VISUAL SOURCE SAFE Contents Working in Teams with CaseComplete... 2 Need an introduction to how version control works?... 2 Exclusive Checkout... 3 Multiple
WORKING IN TEAMS WITH CASECOMPLETE AND MICROSOFT VISUAL SOURCE SAFE Contents Working in Teams with CaseComplete... 2 Need an introduction to how version control works?... 2 Exclusive Checkout... 3 Multiple
CORRELATION ANALYSIS
 CORRELATION ANALYSIS Learning Objectives Understand how correlation can be used to demonstrate a relationship between two factors. Know how to perform a correlation analysis and calculate the coefficient
CORRELATION ANALYSIS Learning Objectives Understand how correlation can be used to demonstrate a relationship between two factors. Know how to perform a correlation analysis and calculate the coefficient
db, dbm, dbw db 10 log (x) where x is unitless! For example, amplifier gain is a unitless value!
 2/15/2005 db.doc 1/9 db, dbm, dbw Decibel (db), is a specific function that operates on a unitless parameter: db log (x) where x is unitless! Q: A unitless parameter! What good is that!? A: Many values
2/15/2005 db.doc 1/9 db, dbm, dbw Decibel (db), is a specific function that operates on a unitless parameter: db log (x) where x is unitless! Q: A unitless parameter! What good is that!? A: Many values
(These instructions are only meant to get you started. They do not include advanced features.)
 FrontPage XP/2003 HOW DO I GET STARTED CREATING A WEB PAGE? Previously, the process of creating a page on the World Wide Web was complicated. Hypertext Markup Language (HTML) is a relatively simple computer
FrontPage XP/2003 HOW DO I GET STARTED CREATING A WEB PAGE? Previously, the process of creating a page on the World Wide Web was complicated. Hypertext Markup Language (HTML) is a relatively simple computer
Notes on Factoring. MA 206 Kurt Bryan
 The General Approach Notes on Factoring MA 26 Kurt Bryan Suppose I hand you n, a 2 digit integer and tell you that n is composite, with smallest prime factor around 5 digits. Finding a nontrivial factor
The General Approach Notes on Factoring MA 26 Kurt Bryan Suppose I hand you n, a 2 digit integer and tell you that n is composite, with smallest prime factor around 5 digits. Finding a nontrivial factor
Linear Programming Notes V Problem Transformations
 Linear Programming Notes V Problem Transformations 1 Introduction Any linear programming problem can be rewritten in either of two standard forms. In the first form, the objective is to maximize, the material
Linear Programming Notes V Problem Transformations 1 Introduction Any linear programming problem can be rewritten in either of two standard forms. In the first form, the objective is to maximize, the material
How to create PDF maps, pdf layer maps and pdf maps with attributes using ArcGIS. Lynne W Fielding, GISP Town of Westwood
 How to create PDF maps, pdf layer maps and pdf maps with attributes using ArcGIS Lynne W Fielding, GISP Town of Westwood PDF maps are a very handy way to share your information with the public as well
How to create PDF maps, pdf layer maps and pdf maps with attributes using ArcGIS Lynne W Fielding, GISP Town of Westwood PDF maps are a very handy way to share your information with the public as well
WORKING IN TEAMS WITH CASECOMPLETE AND ACCUREV. Contents
 WORKING IN TEAMS WITH CASECOMPLETE AND ACCUREV Contents Working in Teams with CaseComplete... 2 Need an introduction to how version control works?... 2 Exclusive Checkout... 3 Multiple Checkout... 3 Merge
WORKING IN TEAMS WITH CASECOMPLETE AND ACCUREV Contents Working in Teams with CaseComplete... 2 Need an introduction to how version control works?... 2 Exclusive Checkout... 3 Multiple Checkout... 3 Merge
How To Write A Hexadecimal Program
 The mathematics of RAID-6 H. Peter Anvin First version 20 January 2004 Last updated 20 December 2011 RAID-6 supports losing any two drives. syndromes, generally referred P and Q. The way
The mathematics of RAID-6 H. Peter Anvin First version 20 January 2004 Last updated 20 December 2011 RAID-6 supports losing any two drives. syndromes, generally referred P and Q. The way
How To Factor By Gcf In Algebra 1.5
 7-2 Factoring by GCF Warm Up Lesson Presentation Lesson Quiz Algebra 1 Warm Up Simplify. 1. 2(w + 1) 2. 3x(x 2 4) 2w + 2 3x 3 12x Find the GCF of each pair of monomials. 3. 4h 2 and 6h 2h 4. 13p and 26p
7-2 Factoring by GCF Warm Up Lesson Presentation Lesson Quiz Algebra 1 Warm Up Simplify. 1. 2(w + 1) 2. 3x(x 2 4) 2w + 2 3x 3 12x Find the GCF of each pair of monomials. 3. 4h 2 and 6h 2h 4. 13p and 26p
Excel macros made easy
 IT Training Excel macros made easy Jane Barrett, IT Training & Engagement Team Information System Services Version 1.1 Scope Learning outcomes Understand the concept of what a macro is and what it does.
IT Training Excel macros made easy Jane Barrett, IT Training & Engagement Team Information System Services Version 1.1 Scope Learning outcomes Understand the concept of what a macro is and what it does.
Developing Physical Solutions for InfoSphere Master Data Management Server Advanced Edition v11. MDM Workbench Development Tutorial
 Developing Physical Solutions for InfoSphere Master Data Management Server Advanced Edition v11 MDM Workbench Development Tutorial John Beaven/UK/IBM 2013 Page 1 Contents Overview Machine Requirements
Developing Physical Solutions for InfoSphere Master Data Management Server Advanced Edition v11 MDM Workbench Development Tutorial John Beaven/UK/IBM 2013 Page 1 Contents Overview Machine Requirements
Intelligent Log Analyzer. André Restivo <andre.restivo@portugalmail.pt>
 Intelligent Log Analyzer André Restivo 9th January 2003 Abstract Server Administrators often have to analyze server logs to find if something is wrong with their machines.
Intelligent Log Analyzer André Restivo 9th January 2003 Abstract Server Administrators often have to analyze server logs to find if something is wrong with their machines.
Credit Card Activity
 Credit Card Activity Introduction: Students will use what they have already learned to create a spreadsheet for the monthly expenses of a credit card. Most students are not very familiar with how a credit
Credit Card Activity Introduction: Students will use what they have already learned to create a spreadsheet for the monthly expenses of a credit card. Most students are not very familiar with how a credit
each college c i C has a capacity q i - the maximum number of students it will admit
 n colleges in a set C, m applicants in a set A, where m is much larger than n. each college c i C has a capacity q i - the maximum number of students it will admit each college c i has a strict order i
n colleges in a set C, m applicants in a set A, where m is much larger than n. each college c i C has a capacity q i - the maximum number of students it will admit each college c i has a strict order i
Year 9 set 1 Mathematics notes, to accompany the 9H book.
 Part 1: Year 9 set 1 Mathematics notes, to accompany the 9H book. equations 1. (p.1), 1.6 (p. 44), 4.6 (p.196) sequences 3. (p.115) Pupils use the Elmwood Press Essential Maths book by David Raymer (9H
Part 1: Year 9 set 1 Mathematics notes, to accompany the 9H book. equations 1. (p.1), 1.6 (p. 44), 4.6 (p.196) sequences 3. (p.115) Pupils use the Elmwood Press Essential Maths book by David Raymer (9H
UK Terms. White Cosmos. Frida s Flowers Blanket Block 1
 UK Terms White Cosmos Frida s Flowers Blanket Block Introduction by Jane Crowfoot I am delighted that Stylecraft asked me to design another Crochet Along project for them following the success of the Lily
UK Terms White Cosmos Frida s Flowers Blanket Block Introduction by Jane Crowfoot I am delighted that Stylecraft asked me to design another Crochet Along project for them following the success of the Lily
The Assumption(s) of Normality
 The Assumption(s) of Normality Copyright 2000, 2011, J. Toby Mordkoff This is very complicated, so I ll provide two versions. At a minimum, you should know the short one. It would be great if you knew
The Assumption(s) of Normality Copyright 2000, 2011, J. Toby Mordkoff This is very complicated, so I ll provide two versions. At a minimum, you should know the short one. It would be great if you knew
US Terms. White Cosmos. Frida s Flowers Blanket Block 1
 US Terms White Cosmos Frida s Flowers Blanket Block Introduction by Jane Crowfoot I am delighted that Stylecraft asked me to design another Crochet Along project for them following the success of the Lily
US Terms White Cosmos Frida s Flowers Blanket Block Introduction by Jane Crowfoot I am delighted that Stylecraft asked me to design another Crochet Along project for them following the success of the Lily
Pigeonhole Principle Solutions
 Pigeonhole Principle Solutions 1. Show that if we take n + 1 numbers from the set {1, 2,..., 2n}, then some pair of numbers will have no factors in common. Solution: Note that consecutive numbers (such
Pigeonhole Principle Solutions 1. Show that if we take n + 1 numbers from the set {1, 2,..., 2n}, then some pair of numbers will have no factors in common. Solution: Note that consecutive numbers (such
Factoring Flow Chart
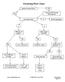 Factoring Flow Chart greatest common factor? YES NO factor out GCF leaving GCF(quotient) how many terms? 4+ factor by grouping 2 3 difference of squares? perfect square trinomial? YES YES NO NO a 2 -b
Factoring Flow Chart greatest common factor? YES NO factor out GCF leaving GCF(quotient) how many terms? 4+ factor by grouping 2 3 difference of squares? perfect square trinomial? YES YES NO NO a 2 -b
Karnaugh Maps. Circuit-wise, this leads to a minimal two-level implementation
 Karnaugh Maps Applications of Boolean logic to circuit design The basic Boolean operations are AND, OR and NOT These operations can be combined to form complex expressions, which can also be directly translated
Karnaugh Maps Applications of Boolean logic to circuit design The basic Boolean operations are AND, OR and NOT These operations can be combined to form complex expressions, which can also be directly translated
desired behaviour (global constraints) composite system putative behaviour: putative agents, actions, etc.
 Ó Ð¹ Ö Ú Ò ÔÔÖÓ ØÓ Ö ÕÙ Ö Ñ ÒØ Ò Ò Ö Ò ËØ Û ÖØ Ö Ò Ø Û Öغ Ö ÒÙÛ º ºÙ Ô ÖØÑ ÒØ Ó ÓÑÔÙØ Ò ÍÒ Ú Ö ØÝ Ó Ø Ï Ø Ó Ò Ð Ò Ö ØÓÐ ØÖ Ø ÒÙÑ Ö Ó Ö ÒØ ÔÔÖÓ ØÓ Ö ÕÙ Ö Ñ ÒØ Ò Ò Ö Ò Ù Ø Ø Ø Ò Û Ô Ö Ñ Ñ Ö Ò ÙÔÓÒ Ø Ù Ó
Ó Ð¹ Ö Ú Ò ÔÔÖÓ ØÓ Ö ÕÙ Ö Ñ ÒØ Ò Ò Ö Ò ËØ Û ÖØ Ö Ò Ø Û Öغ Ö ÒÙÛ º ºÙ Ô ÖØÑ ÒØ Ó ÓÑÔÙØ Ò ÍÒ Ú Ö ØÝ Ó Ø Ï Ø Ó Ò Ð Ò Ö ØÓÐ ØÖ Ø ÒÙÑ Ö Ó Ö ÒØ ÔÔÖÓ ØÓ Ö ÕÙ Ö Ñ ÒØ Ò Ò Ö Ò Ù Ø Ø Ø Ò Û Ô Ö Ñ Ñ Ö Ò ÙÔÓÒ Ø Ù Ó
Constructing Contracts: Making Discrete Mathematics Relevant to Beginning Programmers
 Constructing Contracts: Making Discrete Mathematics Relevant to Beginning Programmers TIMOTHY S. GEGG-HARRISON Winona State University Although computer scientists understand the importance of discrete
Constructing Contracts: Making Discrete Mathematics Relevant to Beginning Programmers TIMOTHY S. GEGG-HARRISON Winona State University Although computer scientists understand the importance of discrete
The mathematics of RAID-6
 The mathematics of RAID-6 H. Peter Anvin 1 December 2004 RAID-6 supports losing any two drives. The way this is done is by computing two syndromes, generally referred P and Q. 1 A quick
The mathematics of RAID-6 H. Peter Anvin 1 December 2004 RAID-6 supports losing any two drives. The way this is done is by computing two syndromes, generally referred P and Q. 1 A quick
CHAPTER 7 RESULT ANALYSIS AND STATISTICS. 7.1 Introduction to manual Vs automated testing
 CHAPTER 7 RESULT ANALYSIS AND STATISTICS 7.1 Introduction to manual Vs automated testing Testing is considered to be the most crucial part of the software development life cycle. It is very important because
CHAPTER 7 RESULT ANALYSIS AND STATISTICS 7.1 Introduction to manual Vs automated testing Testing is considered to be the most crucial part of the software development life cycle. It is very important because
Semantics and Generative Grammar. Quantificational DPs, Part 3: Covert Movement vs. Type Shifting 1
 Quantificational DPs, Part 3: Covert Movement vs. Type Shifting 1 1. Introduction Thus far, we ve considered two competing analyses of sentences like those in (1). (1) Sentences Where a Quantificational
Quantificational DPs, Part 3: Covert Movement vs. Type Shifting 1 1. Introduction Thus far, we ve considered two competing analyses of sentences like those in (1). (1) Sentences Where a Quantificational
SEARCH ENGINE OPTIMISATION
 S E A R C H E N G I N E O P T I M I S AT I O N - PA G E 2 SEARCH ENGINE OPTIMISATION Search Engine Optimisation (SEO) is absolutely essential for small to medium sized business owners who are serious about
S E A R C H E N G I N E O P T I M I S AT I O N - PA G E 2 SEARCH ENGINE OPTIMISATION Search Engine Optimisation (SEO) is absolutely essential for small to medium sized business owners who are serious about
Unicenter Patch Management
 Unicenter Patch Management Best Practices for Managing Security Updates R11 This documentation (the Documentation ) and related computer software program (the Software ) (hereinafter collectively referred
Unicenter Patch Management Best Practices for Managing Security Updates R11 This documentation (the Documentation ) and related computer software program (the Software ) (hereinafter collectively referred
2DI36 Statistics. 2DI36 Part II (Chapter 7 of MR)
 2DI36 Statistics 2DI36 Part II (Chapter 7 of MR) What Have we Done so Far? Last time we introduced the concept of a dataset and seen how we can represent it in various ways But, how did this dataset came
2DI36 Statistics 2DI36 Part II (Chapter 7 of MR) What Have we Done so Far? Last time we introduced the concept of a dataset and seen how we can represent it in various ways But, how did this dataset came
WAGO-I/O-SYSTEM. Using library WagoLibMSSQL_03.lib in CoDeSys 2.3 for interface to Microsoft SQL Server 200x. Application Note
 Application Note Using library WagoLibMSSQL_03.lib in CoDeSys 2.3 for interface to Microsoft SQL Server 200x WAGO-I/O-SYSTEM a302510, English Version: 1.0.0 2 Impressum 2012 by WAGO Kontakttechnik GmbH
Application Note Using library WagoLibMSSQL_03.lib in CoDeSys 2.3 for interface to Microsoft SQL Server 200x WAGO-I/O-SYSTEM a302510, English Version: 1.0.0 2 Impressum 2012 by WAGO Kontakttechnik GmbH
What's Wrong With Formal Programming Methods? Eric C.R. Hehner
 What's Wrong With Formal Programming Methods? Eric C.R. Hehner Department of Computer Science, University of Toronto, Toronto M5S 1A4 Canada The January 1991 issue of Computing Research News includes the
What's Wrong With Formal Programming Methods? Eric C.R. Hehner Department of Computer Science, University of Toronto, Toronto M5S 1A4 Canada The January 1991 issue of Computing Research News includes the
How to import Email Data from Outlook 2007 in standalone mode to your Pushex Exchange mailbox
 How to import Email Data from Outlook 2007 in standalone mode to your Pushex Exchange mailbox Moving to a Hosted Exchange mailbox from using Outlook in standalone mode has many advantages, here are 3:-
How to import Email Data from Outlook 2007 in standalone mode to your Pushex Exchange mailbox Moving to a Hosted Exchange mailbox from using Outlook in standalone mode has many advantages, here are 3:-
Basic ESXi Networking
 Basic ESXi Networking About vmnics, vswitches, management and virtual machine networks In the vsphere client you can see the network diagram for your ESXi host by clicking Networking on the Configuration
Basic ESXi Networking About vmnics, vswitches, management and virtual machine networks In the vsphere client you can see the network diagram for your ESXi host by clicking Networking on the Configuration
Lottery Looper. User Manual
 Lottery Looper User Manual Lottery Looper 1.7 copyright Timersoft. All rights reserved. http://www.timersoft.com The information contained in this document is subject to change without notice. This document
Lottery Looper User Manual Lottery Looper 1.7 copyright Timersoft. All rights reserved. http://www.timersoft.com The information contained in this document is subject to change without notice. This document
Tips for clear websites
 Plain English Campaign: Tips for clear websites Copyright Plain English Campaign Tips for clear websites This is only a basic guide. If you have any suggestions, corrections or improvements, please contact
Plain English Campaign: Tips for clear websites Copyright Plain English Campaign Tips for clear websites This is only a basic guide. If you have any suggestions, corrections or improvements, please contact
SECTION 0.6: POLYNOMIAL, RATIONAL, AND ALGEBRAIC EXPRESSIONS
 (Section 0.6: Polynomial, Rational, and Algebraic Expressions) 0.6.1 SECTION 0.6: POLYNOMIAL, RATIONAL, AND ALGEBRAIC EXPRESSIONS LEARNING OBJECTIVES Be able to identify polynomial, rational, and algebraic
(Section 0.6: Polynomial, Rational, and Algebraic Expressions) 0.6.1 SECTION 0.6: POLYNOMIAL, RATIONAL, AND ALGEBRAIC EXPRESSIONS LEARNING OBJECTIVES Be able to identify polynomial, rational, and algebraic
Maths Refresher. Expanding and Factorising
 Maths Refresher Expanding and Factorising Expanding and Factorising Learning intentions. Recap Expanding equations Factorising equations Identity: perfect pairs Difference of two squares Introduction Algebra
Maths Refresher Expanding and Factorising Expanding and Factorising Learning intentions. Recap Expanding equations Factorising equations Identity: perfect pairs Difference of two squares Introduction Algebra
COMPUTING PRACTICES ASlMPLE GUIDE TO FIVE NORMAL FORMS IN RELATIONAL DATABASE THEORY
 COMPUTING PRACTICES ASlMPLE GUIDE TO FIVE NORMAL FORMS IN RELATIONAL DATABASE THEORY W LL AM KErr International Business Machines Corporation Author's Present Address: William Kent, International Business
COMPUTING PRACTICES ASlMPLE GUIDE TO FIVE NORMAL FORMS IN RELATIONAL DATABASE THEORY W LL AM KErr International Business Machines Corporation Author's Present Address: William Kent, International Business
5 Homogeneous systems
 5 Homogeneous systems Definition: A homogeneous (ho-mo-jeen -i-us) system of linear algebraic equations is one in which all the numbers on the right hand side are equal to : a x +... + a n x n =.. a m
5 Homogeneous systems Definition: A homogeneous (ho-mo-jeen -i-us) system of linear algebraic equations is one in which all the numbers on the right hand side are equal to : a x +... + a n x n =.. a m
Exponents and Radicals
 Exponents and Radicals (a + b) 10 Exponents are a very important part of algebra. An exponent is just a convenient way of writing repeated multiplications of the same number. Radicals involve the use of
Exponents and Radicals (a + b) 10 Exponents are a very important part of algebra. An exponent is just a convenient way of writing repeated multiplications of the same number. Radicals involve the use of
Using simulation to calculate the NPV of a project
 Using simulation to calculate the NPV of a project Marius Holtan Onward Inc. 5/31/2002 Monte Carlo simulation is fast becoming the technology of choice for evaluating and analyzing assets, be it pure financial
Using simulation to calculate the NPV of a project Marius Holtan Onward Inc. 5/31/2002 Monte Carlo simulation is fast becoming the technology of choice for evaluating and analyzing assets, be it pure financial
DEGREE PROGRAMME AND COURSE INFORMATION: A STUDENT S GUIDE TO DRPS
 DEGREE PROGRAMME AND COURSE INFORMATION: A STUDENT S GUIDE TO DRPS This guide explains how to use the University s DRPS (we ll explain the acronym in a moment) to help you understand your Degree programme
DEGREE PROGRAMME AND COURSE INFORMATION: A STUDENT S GUIDE TO DRPS This guide explains how to use the University s DRPS (we ll explain the acronym in a moment) to help you understand your Degree programme
DVBLink For IPTV. Installation and configuration manual
 DVBLink For IPTV Installation and configuration manual DVBLogic 2010 Table of contents Table of contents... 2 Introduction... 4 Installation types... 4 DVBLink for IPTV local installation... 4 DVBLink
DVBLink For IPTV Installation and configuration manual DVBLogic 2010 Table of contents Table of contents... 2 Introduction... 4 Installation types... 4 DVBLink for IPTV local installation... 4 DVBLink
Section 5: Installing the Print Driver
 Section 5: Installing the Print Driver In This Section Print Driver Installation for USB Connection Using the Ethernet Connection and a Crossover Cable Print Driver: The Epilog print driver is the software
Section 5: Installing the Print Driver In This Section Print Driver Installation for USB Connection Using the Ethernet Connection and a Crossover Cable Print Driver: The Epilog print driver is the software
(Common) Shock models in Exam MLC
 Making sense of... (Common) Shock models in Exam MLC James W. Daniel Austin Actuarial Seminars www.actuarialseminars.com June 26, 2008 c Copyright 2007 by James W. Daniel; reproduction in whole or in part
Making sense of... (Common) Shock models in Exam MLC James W. Daniel Austin Actuarial Seminars www.actuarialseminars.com June 26, 2008 c Copyright 2007 by James W. Daniel; reproduction in whole or in part